Infrastructure Management Services
Overview
Infrastructure Management Services
atom’s IT Infrastructure Management Services (IMS) offers a suite of reliable, responsive, flexible and proven infrastructure services and solutions that deliver differentiated value to our customer’s business.
Our rich portfolio of service offerings span across the infrastructure lifecycle of Plan-Build-Run-Monitor and includes infra Consultancy, data center, end user computing, enterprise networking, enterprise security, IT infrastructure operation management and transformation services.
The IMS team with experts in 36 countries, an ecosystem of strong alliances and a Delivery & Data Center footprint across continents helps us provide true 24X7 services to over 190 customers in multiple industries such as Telecom, Banking, Manufacturing, Insurance, Retail and Healthcare. We continue to invest in multiple proprietary initiatives such as atom’s USOP (Unified Service Operations Platform), IMS Academy and IMS NWS (New World Solutions) that help us constantly innovate and deliver differentiated and incremental value to our customers.
- Breadth and depth of offerings that are proven
- Deep domain expertise in Verticals across Telecom, Banking, Manufacturing, Insurance, Retail and Healthcare
- Multiple engagement models with shared risks and rewards
- Ability to scale as you grow – our single largest engagement is of 1400+ FTEs managing 75K+ Servers, 25 PB Storage, 35K Network Elements, 1700 Applications.
- Investments in platforms, tools and a robust ecosystem of alliances that help us deliver differentiated value
- We enable our customers win:
- Our VDI implementation at a Large Australian Bank won IDC Enterprise Innovation Award
- Our client, an Indian Banking major, was awarded as the “best internet banking site” in India by IBA
- atom group ecosystem leverage for best practices
- Partners with best-of-breed technology providers
- Analyst Endorsements
- Positioned in Gartner’s MQ for DC & IUS, Americas for the 3rd time in a row
- Featured in Forrester’s Wave for “Global IT Infrastructure Outsourcing”
- Reliable: Best-of-breed products and processes, Quality certifications, stringent audit checks, world-class assets and a robust training methodology ensure our services are reliable and are delivered first-time-right
- Responsive: One of the key values we stand for is ‘Customer First’. Be it solving a problem, addressing a situation, exploring a new technology or stepping out of comfort zone, we are quick to respond. No surprise we designed and deployed a Tier 2 Datacenter for one of our customers in just 90 days!
- Flexible: Be it engagement models, pricing options, choice of delivery locations, roadmap for infra transformation or adoption of new technologies, we offer multiple and granular options for our customers to choose from
- Proven: Serving over 190 customers with average engagement tenure of over 6 years. Managing over 75+ Data Centers. Large SoC Operations delivering to 450+ enterprise clients. Our engagement with some of our long serving customers is as old as we are in this business!
- Future-ready infrastructure-: Our experiences, best practices and investments deliver unprecedented scalability
Peace of mind: Holistic and integrated security offerings that secure every aspect of the IT landscape - Flexibility: Multiple engagement and delivery models with a choice of pricing options
Stay ahead with Smart Infra management – Investments in automation and next generation IT Operations leveraging USOP
Savings: Guaranteed YoY savings through transformational service delivery approach including asset monetization
Experience
- Manage 70+ Data Centers, 650,000+ assets, 80+ PB of data
- Over 15 years of providing Hosting Services from Atom’s Data Centers
- 5+ Years engagement on Workspace-as-a-Service for 20,000+ users
- Operate multilingual service desk
- SOC services for over 450+ enterprise customers
Unique Scale
- Largest Infra Management engagement with 1400+ FTEs managing 75K+ Servers, 25 PB Storage, 35K Network Elements, 1700 Applications
Investments in Innovation
- IMS Academy: Unique simulation-based infrastructure operations training program
- Pioneers in transforming traditional desktops to WaaS in a private Cloud model
- Unified Service Operations Platform (USOP): A next generation automation and service management platform
Differentiated offerings
- Workspace- as- a-Service (WaaS): Transforming traditional desktops to workspaces in a private cloud
- Managed Platform for Adaptive Computing (mPAC): Enabling a secure transformation leveraging the cloud
- Mobile Device Management (MDM): Enabling BYOD
- Modular Enterprise Managed Services (mEMS): Simplifies enterprise network management leveraging Cloud-based platform
Service Offerings
Overview
With a comprehensive Infrastructure Management Services portfolio we help you achieve newer levels of business performance and enable you to derive more from your IT investments. Working with leading global alliances, atom brings in agility, efficiency and experience in managing critical IT infrastructure..
Snapshot of global IMS engagements :
- End to End Infrastructure Outsourcing support for US Tier 1 Telecommunication Major
- Hosting And Managed Infrastructure Services for leading manufacturer of ball and roller bearings
- DC Consolidation & Management for Leading UK Health Service Provider
- Complex Transition & E2E DC Management for Leading US Telecom Service Provider
- Data Center Transformation for Leading Telecom Provider in Australia
- Server monitoring, Desk side and Middleware support for US Financial Major
- Asset management for Global Sports Major
- End to End Infrastructure Outsourcing support for UK Media major
- Data center Operations for Chemical Manufacturing Company
- Global Infrastructure outsourcing Partner for a leading IT Services company in Denmark
- Transformation solution support for leading Indian Financial Services Group
- Total Infrastructure outsourcing deal for UK major Insurance Provider
- MS Lync implementation for a Indian multinational telecommunications provider
- WaaS service for American managed health care Provider
- DBMS Maintenance & Production Support for Global Automobile Major
- WaaS & Desktop support for Netherlands Telecom Major
Data Center
atom recognizes the importance of Data Centers in an organization’s ability to succeed and regards it as a ‘Value Center’ where the blue print of the business resides.
Organizations are looking at ways to meet the IT demands of business while providing innovative services that give them business agility and competitive advantage. One of the key focuses of atom’s DC Transformation and Operation services is the dynamic alignment of business requirements and IT systems that deliver efficiencies that drive down costs, optimize resources, and enable innovation.
Top Down Approach
atom realizes that there was a time when business decisions were limited if not dictated by the capabilities of the data center. This “Bottom-Up” approach is being rapidly replaced by the “Top-Down” approach.
This “Top Down Approach” for transformation that atom has embraced and imbibed in its approach aligns business and IT by embracing a real-time infrastructure and enabling executives to make strategic business decisions knowing they are supported by IT.
Plan & Consult
DC Consultancy & Assessment
- DC Facility Assessment
- Infrastructure Assessment
- Cloud Consultancy
- DR Consultancy
Transform & Build
Managed Services
- Remote Infrastructure Management
- Data Center Management
- Server Management
- Storage Management
- Backup and Arch Management
- Web Server Management
- Database Management
- Mainframe Operations
Database Services
atom’s Database Administration (DBA) Service is a comprehensive offering with cradle to grave data support, skilled database administration and meticulous capacity planning. atom uses unique RightSourcing and global delivery models to deliver holistic database management services of the highest quality, meeting extremely tight service level agreements.
atom’s portfolio cuts across the entire spectrum of DBA services and phases of database life cycle:
- New Database Technology Evaluation PoCs for emerging technologies and solutions like DB Virtualization, Cloud Based solutions and Big Data solutions
- Database Environment Setup Database Set up; Implementation and Configuration of High Availability, DR and Security solutions
- Database Security Management Data Encryption/Masking and DB Security Audit Compliance
- Database Environment Management Database Monitoring, Routine Administration and Maintenance, Technical Troubleshooting, Backup and Recovery, Incident and Service Request Management,
- Documentation and Reporting Database Performance Optimization Database Audits (Database Architecture, Parameters,
Backup Policy), Performance Tuning, Upgrades and Migrations - Database Upgrade and Migration Database Upgrades, Cross Platform Migrations, Cross
- RDBMS Migration
- Database Environment Transformation Legacy System Modernization, Database Consolidation, DB Virtualization, Migration to DB Appliances, DW Remediation
DBA competency Highlights:
- Over 6000+ person years of delivery experience
- 1200+ Strong DBA workforce supporting all major DMBS products viz., Oracle, MS SQL Server, Teradata, DB2 UDB, DB2 Z/OS, Sybase, Informix, MySQL
- 100+ active customer engagements
- 700+ projects delivered successfully across consolidation, installation and migrations
- Over 50 managed services support engagements for highly complex, heterogeneous database environments
- Defined Accelerators including Six Sigma based Transition Toolkit, database support methodology, KEDB, KPIs, service improvement plans, templates & checklists
- ITIL V3.0 based service delivery platform
Benefits
- Year-on-year productivity improvement of 10% through tools, better knowledge management and automation
- Capex reduction of 12-15% over a period of 3 years by leveraging DB consolidation, storage/license
- optimization and virtualization
- Incident Ticket volume reduction of 10% due to proactive maintenance, problem management and database environment stabilization
- Up to 17% reduction of ticket handling time by process streamlining and standardization
Adoption of global best practices
atom Hosting Services
atom has over 7 years of delivering ‘availability experience’ and ‘managed hosting services’ leveraging its highly reliable and scalable Datacenters across the globe.
Managed Hosting Services allows companies to slash their investments in IT infrastructure, facilitate quicker deployments and implement a streamlined SLA driven infrastructure. It enables companies move from a Capex to an Opex business model, giving them business agility and flexibility.
Virtualization of application through a private cloud deployment yields Opex savings between 40-50%. It also gives companies turnkey infrastructure, reducing deployment times from months to days
atom’s Managed Hosting Services comprise of:
- Cloud Hosting
- Utility Hosting
- Dedicated Hosting
- Hybrid Hosting
- ERP Hosting
- Smart Asset Hosting for
- Virtual Desktop Infrastructure (WaaS)
- Mobile Device Management (MDM)
- Big Data
- Social Networks
- Search Engines
- Disaster Recovery Services
- Colocation Services
- Asset Monetization
End-User Computing
atom EUC capabilities and offerings focus on enabling enterprises to achieve their business objectives through the effective management of their end user computing resources. Our comprehensive & robust services focus on key desktop management functions that can be delivered remotely to support a customer’s complex desktop and mobile computing environment. The services address the most common management and support tasks in an automated, centralized manner.
Our End-User Computing services includes Transformation solutions, Desktop Management, Service deck, Device Management, UCC and last-mile support. With significant investments in voice infrastructure, we deliver cost-effective Service Desk through our Global Delivery Centers.
Our End-User Computing portfolio includes:
End User Transformation
Transforming to a futuristic infrastructure
Today IT is expensive, unresponsive and consumes vast amount of capital, delivering resources which eventually are grossly underutilized. Leverage the power of atom end user transformational solutions while retaining the flexibility and open standards to support your existing IT infrastructure to be more efficient, flexible and cost –effective. The transformation solutions help you in seamless migration from the current (legacy) infrastructure into which is now called as ‘Next Generation Infrastructure’
Workspace as a Service (WaaS)™
Access your workspace securely … anywhere, anytime, any device!
End User Computing or Workspace Computing is in the process of being redefined. Traditional client computing devices such as desktops and laptops have had their share of cost and management challenges. The new world demands of device independence, anywhere anytime access and data security, are forcing enterprises to evaluate alternate solutions.
atom Workspace-as-a-Service (WaaS) offers a unique way for customers to embark on the virtual workspace computing journey allowing dedicated, pooled or shared virtual desktops or applications to be accessed any time from anywhere using any device.
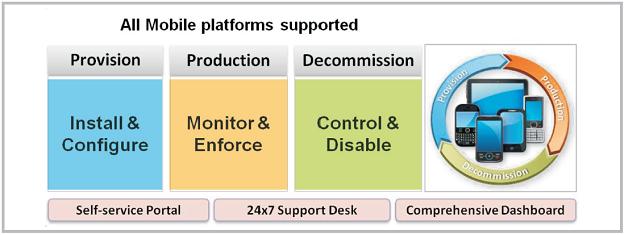
Key Business drivers
- Enterprise- Employee agility
- Secured environment
- Reduced Capex
- Centralized management
- Bring -Your-Own – Device (BYOD)
- Go Green
Solution Insights
MDM Mobile Device Management
Go Mobile….fast & secure
Managing and securing multiple mobile devices in a corporate environment has been a huge challenge. The challenge is compounded with newer and more capable mobile devices being launched in the market very often. This growing adoption of smart mobile devices is leading to an expectation from IT to support them seamlessly.
Tech Mahindra’s Mobile management service offers a unique way of managing the corporate mobile devices using a single unified management console, a suite of plug and play ITIL-based software modules and enhanced mobility experience while solving your most pressing mobility challenges.
MDM Offering includes :
- Secure and control mobile access to company assets throughout the full mobile lifecycle, ‘from cradle-to-grave’
- MDM planning and assessment
- Hosted or on-premise Managed services for End-user Support and Helpdesk
- Order and Spend Management solutions
- MDM migration services
- Implementation and support services
Messaging Platform Services
Smartest way to upgrade your Messaging infrastructure
As the business is growing there is continued demand for the highly reliable messaging platform. There is continuous demand to reduce cost, reduce IT management cost and optimize user productivity. The users can’t afford a downtime for the Messaging platform, even during Migration. atom’s provides an end to end solution for Messaging Platform Migration which can help in addressing business challenges.
Messaging Platform Services
- Microsoft Exchange 2003/2007 to Exchange 2010 Migration
- Microsoft Exchange 2003/2007 and Office 365 Hybrid Solution
- Lotus Domino to Microsoft Exchange Migration
- On-Premise to Office 365 Migration
- On-Premise to Google Apps Migration
Windows 7 and 8 Migration Services
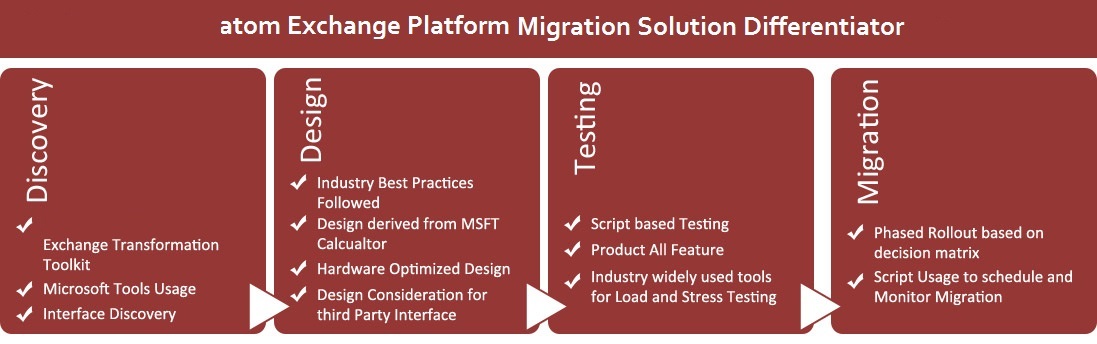
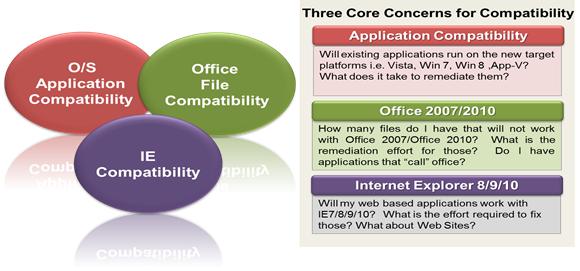
Windows XP support is ending in April 2014. Seek “WIN7/8-MigR8” support from atom now and migrate all your desktops to Win7/8 in a hassle free manner! WIN7/8 is atom one stop migration service spread over 5 phases of namely 1) Assessment 2) Testing and Remediation 3) Packaging 4) Image management 5) Deployment. It consists of an array of service offerings
Consultancy:
- Assessment of compatibility of Application and Hardware environment.
- Creation of suitable application handling techniques, deployment strategies and support mechanisms.
Global Packaging Factory services:
- Application compatibility testing
- Application packaging
- Application virtualization
- Image creation
- Image deployment
- Application deployment
- Post deployment support
Organizations Concerns:
At atom we have optimum solutions for all your concerns.
Move and Save advantage of WIN7/8-MigR8 :
- The centrally managed PC settings standardized desktop strategy and comprehensive PC security along with compatibility testing via automation tools implies an immense cost saving opportunity.
- atom has a huge team of migration experts well versed in Windows 7/ 8 deployment as well as latest tools by Microsoft. So, why delay? Contact us now!
Application packaging services
We deliver Application Packaging and deployment services to clients from our Global Packaging Factories located in Chennai and Hyderabad, India. Global Packaging Factory (GPF) is a unique centre, which aims at supporting the packaging needs of multiple clients. Our Global Packaging Factory has the right People, Infrastructure and Processes in place to perform packaging for high volume of applications at low costs. In GPF, We employ a “factory” approach that includes highly repeatable and standardized processes to package the applications. A factory approach provides not only higher success rate but also enables packages to be processed more rapidly at very competitive costs.
We designed Global Baseline Standards for Application Packaging Environment which can be used for all enterprise customers globally. Thus our Global Packaging Factories (GPFs) provide:
- Centralized Packaging for multiple clients
- Optimized Resource utilization
- Standardized packaging processes
- Global Competence
- Automated tools
- Utmost cost and time effectiveness
- Top class quality assurance
Salient Features:
- Plug Easy & Play Quick” mode.
- Presence of sophisticated infrastructure, Packaging and deployment tools implying direct cost savings to customers
- Low cost of operations derived from optimized mix of resources and tools
- Effective usage of tools with year on year productivity
- Improvements
- Requirement-based resource ramp-up to cater to the dynamic business volumes from customers
- High productivity and excellent quality of application packaging services
Overview
NTSS offers end-to-end network lifecycle services and solutions, enabling Telecom Services Providers (Telcos) and Managed Services Providers (MSPS) build and manage their wireless and wire-line network infrastructure.
NTSS solutions enable the infrastructure to interact with internal and external information technology systems such as Operations Support System (OSS) and Business Support System (BSS) to provide full lifecycle management solutions to Communication Service Providers (CSPs). NTSS services span across the entire network ecosystem for telecom companies and enterprises ranging from network build, operate and maintain in an optimized and cost effective way. It also facilitates integration with Value Added Service platforms thereby achieving business efficiency and excellent customer experience.
NTSS offers full network lifecycle services such as network design, planning, deployment and network operations (maintaining and optimizing communication networks), which help deliver voice, video and data services. Our portfolio of network solutions and services offered by NTSS, can be broadly classified as:
- Carrier Network Services
- Next Generation Networks
- Network Platforms and Applications
- Enterprise Managed Services
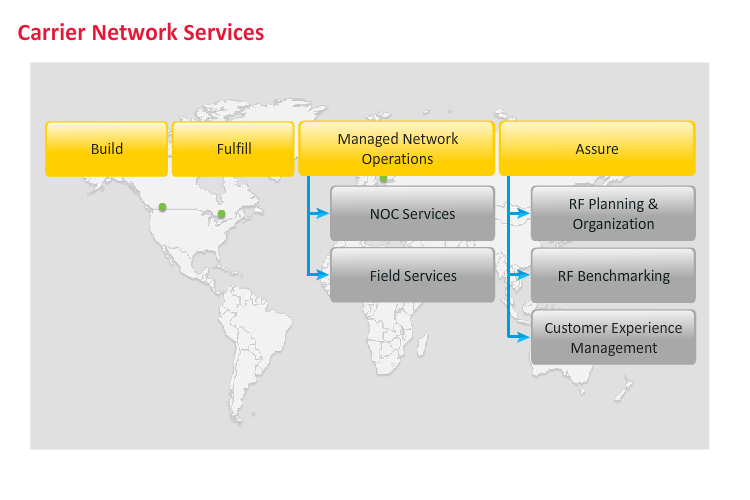
Carrier Network Services
Overview
The Carrier Network Services group provides network build, deployment, service fulfillment and management of the customers’ networks. We have extensive experience in providing optimized services to Greenfield and Brownfield telecom operators through managed network operations.
NTSS aids Telecom Equipment Vendors (TEMs) help their customers achieve quicker launch of products and faster rollouts through our innovative business models to ensure more stable, secure and compliant networks. Our proven benchmarking and optimization expertise improves customer experience and reduces the total cost of ownership.
The Key Portfolios of the Carrier Network Services Group are:
- Build
- Fulfill
- Managed Network Operations
- NOC Services
- Field Services
- Assure
- RF Benchmarking
- RF Planning & Optimization
- Customer Experience Management
Next Generation Networks
Overview
The Next Generation Network group is focused on delivering cutting edge technology solutions in the telecommunications domain. Our technology focus is in the Convergence market with Frameworks and Services in Digital Television, Internet Protocol Television (IPTV), Over-The-Top (OTT), Service Delivery Platform, IP Multimedia Systems and Converged Networks. The group has significant expertise in both legacy and next generation environments in terms of network technology, customer services and business processes.
Our wide-ranging innovative portfolio of integrated solutions and services, expertise in software covering development, integration, testing and maintenance or sustenance services, enables service providers to successfully manage Next Generation Networks. It allows Service Providers, Equipment Vendors and Independent Software Vendors take full advantage of market opportunities to address current and future challenges in the marketplace.
We have successfully designed solutions aimed at major transformation programs for Tier 1, 2 and 3 service providers from legacy to commercial-off-the-shelf (COTS) application for next generation services using our structured approach and robust execution methodology. Our in-house ready-to-deploy components and plug and play of best-of-breed COTS products help reduce the timelines for implementation.
Our Offerings include:
- Next Generation Service Delivery Solution
- IP Multimedia Subsystem E2E Solution
- Video Delivery Solution
- Over The Top – Solution as a service
Next Generation Service Delivery Solution
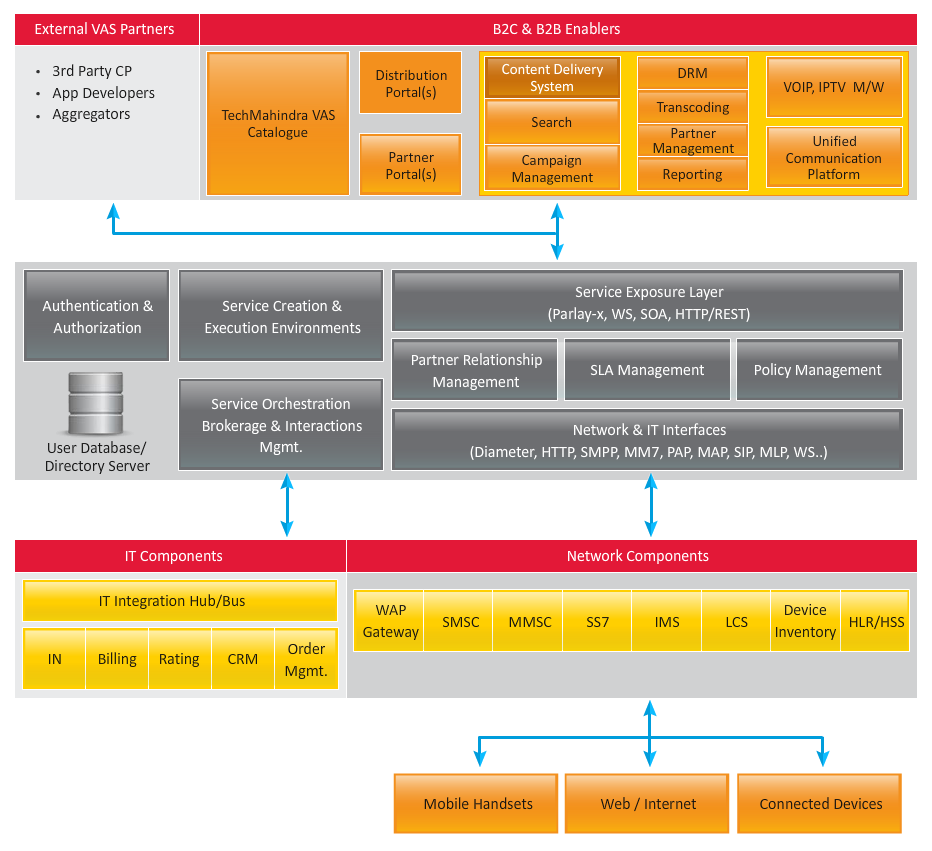
The Service Delivery Platform (SDP) solution provides pre-integrated products such as Communication Middleware Platform, Content Management Platform (CMS), Digital Rights Management (DRM) and Transcoding solution. SDP solution enables Communication Service Providers to quickly monetize network through convergence, by bringing 3rd Party applications and content partners and ease information technology integration.
The Commercial-off-the-shelf (COTS)-based SDP and CMS solution enable the following during the audit of existing network:
- End-to-end SDP and CMS solution deployment for Long Term Evolution (LTE)
- Migration to next generation SDP by replacing end-of-life Service Control Points (SCP) with Next Generation Internet Protocol-based network infrastructure (NGIN)
- Enablement of innovative application
- Managed services of SDP solution
Next Generation Service Delivery Solution Architecture
Key Differentiator
- Our SDP Reference Architecture
- Understanding and implementing network or services topology
- Analyzing existing network or services for performance and bottlenecks
- Identifying Key Performance Indicators (KPIs) and performance parameters
- OSS Counters and other databases
- Application Factory (VAS Catalogue)
- Developed rich Value Added Services (VAS) catalog for enterprise and consumers segments using service exposure layer
- Developed partner on-boarding framework that allows Communication Service Providers to quickly on-board 3rd party partners and applications in the eco-system
- Technology Enabling Monetization on Long Term Evolution (LTE)
- Enablement of Next Generation Services such as Voice over LTE(VoLTE), Rich Communication Services, Centrex(RCS), Web 2.0
- Leverage External Innovation – Wholesales to 3rd party ecosystem
- Monetizing bandwidth with Service Level – Charging and Policy Management – Policy and Charging Rules Function(PCRF)
Internet Protocol Multimedia Subsystem E2E Solution
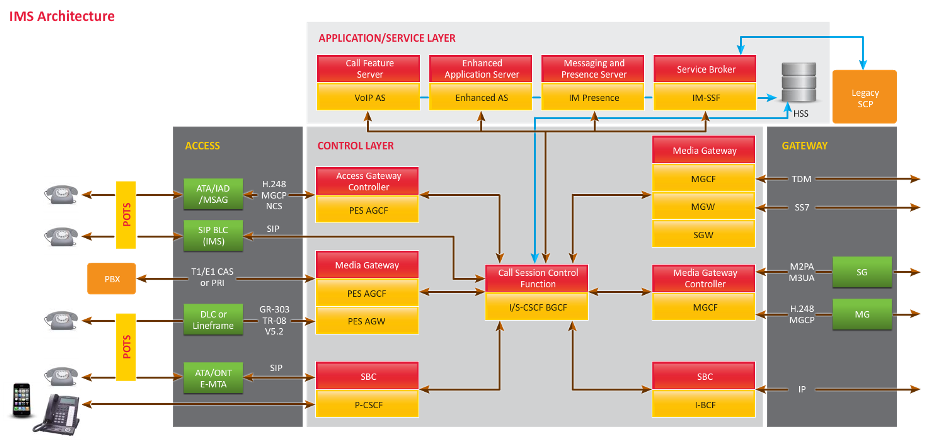
Internet Protocol Multimedia Subsystem E2E Solution
Internet Protocol Multimedia Subsystem (IMS) is a standardized Next Generation Networking (NGN) architecture for telecommunication service providers. It enables transformation of their carrier networks and services to Internet Protocol (IP). With partnership with vendors, we will assist service providers achieve this goal of end-to-end transformation to IP using IMS.
End-to-end network transformation journey undertaken by service providers would enable us to position the Multimedia Testing and Managed Services capabilities.
IMS Architecture
Key Differentiator
- Design, Build, Operate and Test (DBOT) Capabilities for IMS Solutions
- Turnkey deployment of vendor IMS solution in close collaboration with vendors
- Leverage expertise build through end-to-end integration testing project to take ownership of entire multimedia quality assurance (QA) lifecycle of IMS deployments
- Delivers converged applications that increase revenues and subscriber loyalty in both legacy and next-generation networks through integration with Session Initiation Protocol (-SIP) application server
- Technology Enabling Monetization on LTE
- Enablement of Next Generation services such as VoLTE, RCS, through integration with next generation SDP and IMS network
- Improved Efficiency & Cost Saving
- Speeding time-to-market through the quick implementation of new services or by taking advantage of multiple network capabilities
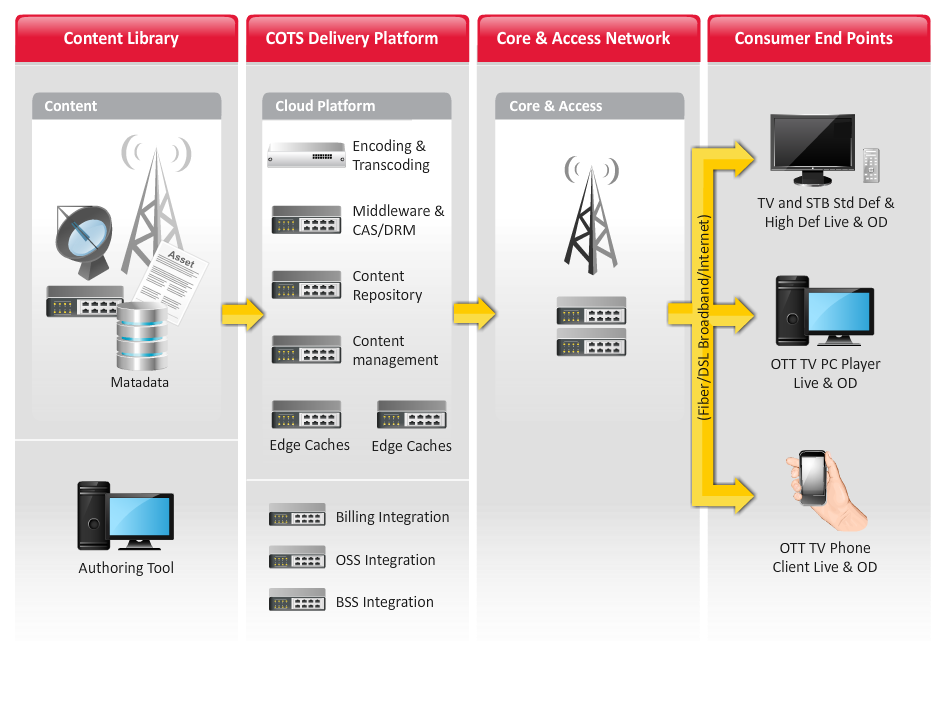
Video Delivery Solution
Video Delivery Solution
Internet Protocol Television (IPTV) enables service providers to fulfill the video aspect (Live and On-Demand) of Triple Play services while providing interactivity (two-way communication) and high quality content for enhanced user experience.
Over the Top (OTT) leverages adaptive streaming technologies such as Apple HLS and Microsoft Smooth Streaming to deliver Live TV and On-Demand content to 3-Screens such as Set Top Boxes (STBs), personal computers (PCs) and mobiles or tablets over the internet (unmanaged network). This enables Service Providers to bring in additional revenue by offering the content that they own as well as external content to any device connected to broadband.
Our offerings include turn-key deployment of Microsoft Mediaroom or commercial off-the-shelf (COTS) based IPTV and OTT solutions. It includes architecture, design, information technology integration, supplier management, application development, managed services and support.
Key Differentiator
- Our pre-integrated ecosystem architecture reduces integration hassles and ensures faster time to market of IPTV services for Service Providers opting for COTS based solution or Microsoft Mediaroom based solution.
- Our ability to build Value-Added Applications over the IPTV stack provides convergence (IPTV-IP Telephony or IPTV-Emails, IPTV-Internet based Social Networking Apps) across the Triple-Play stack while offering convenience to subscribers to manage their services and interact with friends and family from their TV screens. We have also built an Application Abstraction Framework (TAAF) on top of Mediaroom Application Programming Interfaces (APIs) for quick development of Value-Added applications and integration with information technology systems for Mediaroom deployments.
- Cloud based Content Delivery Networks (CDN) and multi-tenancy model allows Service Providers to reduce their capital expenditure (CAPEX) investments significantly. Also, it reduces the time to launch new services in the market. The Managed Services model for CDN ensures Service Providers can concentrate on the core business of selling content to subscribers while we take care of managing and maintaining the CDN for them.
- Mediaroom-Juniper CDN pre-integrated solution offered by the company allows Service Providers to reach out to 3-Screens. It increases the throughput capacity of the Mediaroom platform by its ability to support a huge number of concurrent streams.
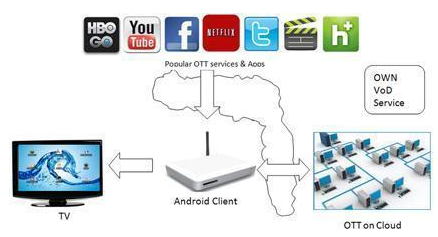
Over The Top - Solution as a Service
Offering description
- It is an in-house created and hosted Solution as a Service, based on Open-Source components. It enables operators to orchestrate the consumption of 3rd party Over the top (OTT) contents and services as well as offer their own content
- It supports “two-side business model”, is telecom centric and can integrate with existing services
- It enables the operator to own and manage the service through dedicated portals
- It allows possible monetization opportunities for operators through:
- Localization and customization of screen real estate and popular OTT services and contents
- Application repository that can leverage popularity of ready 3rd party applications and limit development efforts to high value custom applications
- Exclusive management of application deployment to subscribers
- Support own or 3rd party Video on Demand (VoD) services
- Targeted advertising based on usage statistics
- It provides an option to host the solution on operators’ infrastructure
- It provides an option for operations management
- It provides an option to create custom applications
Key Differentiator
- Ready hosted solution for quick start, requires no investment in infrastructure and scales at operators’ own pace
- Power to orchestrate popular OTT services or application and the screen real estate for realization of business-to-business, businesses-to-consumer and advertisement-based revenue opportunities
- In-house created core solution that is flexible to operator needs and various engagement models
- Innovative Application repository * for managing deployment of various popular applications such as Facebook, Twitter, YouTube, Picassa , WhattsApp, Skype-Video etc
- Solution for not just OTT video alone but multiple applications
- Supports Cheap CPEs* such as smart televisions and consumer electronics devices available over the counter
(* Android based)
Services
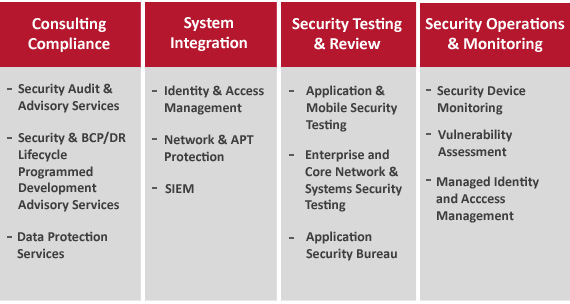
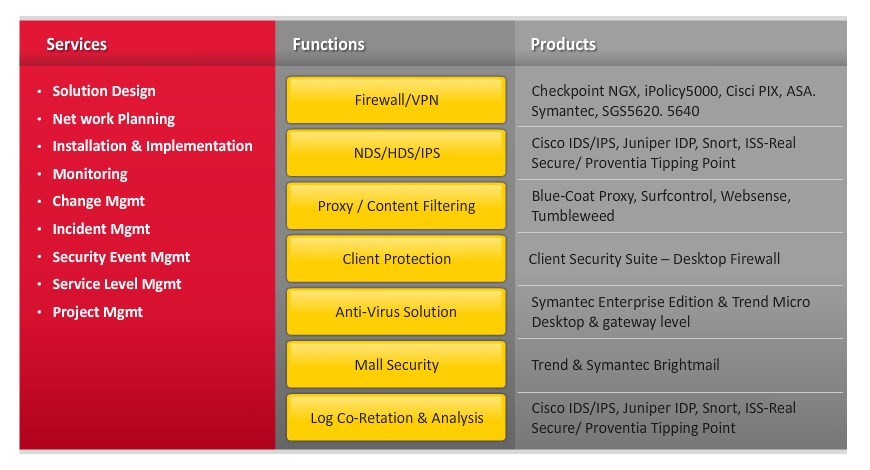
Our value-based partnership approach has been designed to provide our customers with reputation protection, asset protection and compliance. This is achieved through services across the following four categories.
- Consultancy and Compliance services, where we carry out IT risk assessments and benchmarking of organizational security against international standards and best practices. We also help design security frameworks, policies and procedures to uplift the security maturity of an organization
- System Integration services, where we deploy and customize security products across the application estate and network infrastructure
- Security Testing and Review services, where we test the compliance and adherence of enterprise, web and mobile applications to organizational security policies, regulatory requirements and industry standards
- Security Operations and Monitoring services, where we provide round-the-clock management and monitoring services for security infrastructure
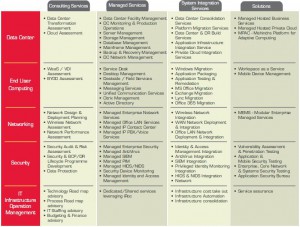
Individual services under these categories are listed in the table below.
Additional detail on key services is available from the links below
- Consultancy and compliance
- System integration
- Identity and access management
- Enterprise and mobile application security testing
- Network and system security
- Managed security services
Preparing for the future
Security has to constantly keep pace with advancements in technology. As our customers adopt newer technologies to do their business, we invest in developing new solutions or extending existing solutions to provide them with continued security cover for their business activities. Some of the areas where we are exploring new solutions include:
- Converged Authentication: Enabling organisations to provide a superior user-experience for their customers by giving them a single method to identify and authenticate themselves irrespective of the channel they use to transact. For instance, banking customers who have to remember multiple passwords for online banking, phone banking and for branch-based services, can now get authenticated using a single mechanism
- Mobile Apps’ Security: With smartphones crossing the boundaries between personal and professional use, mobile apps that power the ubiquitous smartphones are also a key focus for malware. We offer a hosted service that scan mobile apps for the potential rogue behaviour, and our mobile R&D team continues to optimise the detection heuristics to stop even potential zero-day attacks.
Service Offerings
Consultancy & Compliance
Security Governance Compliance
With the exponential increase in digitization of information, regulators have opted for stringent data privacy and fraud prevention measures. Customers have become increasingly conscious of data security, and direct the organizations to include Information Security (IS) as cost of doing business.
Most large organizations have security and business continuity systems and process in place. These systems have grown over time and have been influenced by the perception of security among different function owners. New regulations have built another layer of patchwork for risk compliance
Since security systems have become expensive to maintain, they are inconsistent across the organizations and are not fully compliant to best practices. Alignment of existing security processes with broader organizational initiatives such as Control Objectives for Information and Related Technology (COBIT) and Information Technology Infrastructure Library (ITIL) requires more effort and investment.
We have comprehensive suite of Security Governance, and Risk and Compliance services that assist organizations to review the security framework and the operational controls and to continuously assess and manage the security level.
Our Security Governance and Compliance Services ensure that your organizations security framework is aligned to the business objectives. Our services will help organizations to achieve:
Unified assessment for security, business continuity and information technology service management
Smooth integration of Security framework with the information technology and business initiatives
Certification to international standards such as International Organization for Standardizations ISO 27001
System Integration
System Integration
We know from our experience gained in several large-scale security system integration projects, that an optimal system integration strategy is crucial to the overall success of the business. We have the right tools, templates and industry best implementation methodologies to meet customers information and data security requirements. We offer a complete set of services in the following areas:
- Endpoint security
- Network security
- Identity and Access Management (IAM) implementation
- Content and Uniform Resource Locator (URL) filtering
Log management
The telecom sector faces major challenges such as adopting complex technologies, ever changing business environments and reducing cost. Telecom companies often lack solutions to match the evolution of new technologies and changing business requirements.
We provide system integration expertise to ensure that the technology is strategically aligned to meet the business objectives regardless of the size and nature of the organization.
Our certified processes and service experience indicate the success achieved in executing large turnkey security system integration projects. Our strategic alliances with leading technology players enable us to deliver cost-effective integration services that are steady, scalable, effective, efficient and innovative.
Enterprise & Mobile Application Security Testing
Application Security Consultancy
Security of application assets is a prime concern for organizations. Lack of appropriate application security controls leads to regulatory non-compliance, business continuity failures and data compromise. An effective end-to-end set of services establishes a holistic application security baseline that mitigates risk.
Our services help enhance the security posture of application assets by systematic reviews and assessments. Our Application Security Services ensure a secure application estate by:
- Identifying and prioritizing the high-risk application assets based on business impact and security vulnerabilities
- Assessing the security level of the application systematically throughout the build cycle
- Establishing a security assurance gate to ensure that the new application code and products are assured prior to deployment
- Ensuring a holistic perspective to application security from business requirements to software coding to operations
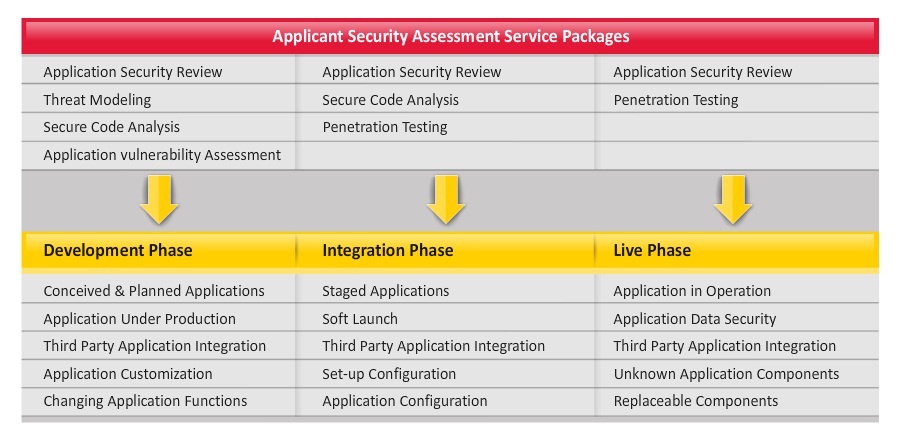
Our Application Security Consultancy Services include:
- Application Estate Security Review
Application Estate Security Review is a high-level review to identify and prioritize the high risk application assets within your application estate. The application estate constitutes the business solution consisting of a set of applications, application infrastructure, business workflows, application technologies, organizational strategies and policies, compliance needs, processes, application security governance and operational procedures.
A high-level application estate security review covers the risk compliance and business security system requirements. As integral parts of the application lifecycle, the review secures the development best practices and operation security application frameworks for identity, access, business continuity and monitoring.
- Application Security Assessment
Application Security Assessment is a consultant-driven detailed analysis of an application security.It covers application risks within requirements, code, security control implementation and application infrastructure. Our consultants use a combination of techniques such as Threat Modeling, Code Analysis, Vulnerability Assessment and Penetration Testing. These techniques are used to identify application security vulnerabilities, risk levels and mitigation steps. Our assessment services can be combined with the Application Estate Security Review to provide a holistic view and roadmap.
Application Security
Application Security review covers a detailed assessment of security requirements, architecture and design, implementation, testing plan and deployment and application infrastructure and components.
Threat Modeling
A Threat Model assesses an application or its components for potential threats to provide threat ratings based on the criticality of the threat and possible attack exposure. Our process comprehensively records all the application components such as entry points, exit points, dependencies, information and data flow, user roles, protected resources, attack path and mitigation objectives.
Secure Code Analysis
Security Code Analysis is a comprehensive security assessment and analysis of application code that focuses on application security considerations, such as secure programming, business-driven application security policies, information protection needs, authentication needs, access controls, authorization and trusted computing needs.
Application Security Testing
An application and its components are inspected for level of their resilience to possible application security threats. Application Vulnerability Assessment identifies the security issues that may expose the business to risk due to internal threats. Penetration Testing identifies vulnerabilities in the web applications that could be exploited through internet facing components.
Application Security Assurance Service
Application Security Assurance Service involves setting up of comprehensive security gate within our customer’s environment, which analyzes the application estate for vulnerabilities, threats and risks. Our service provides recommendations for risk mitigation using a combination of assessment service components. The assurance service provides a periodic assessment of the application estate security posture to maintain the business risks to minimum.
Network and System Security
Network System Security
Large organizations use network security systems such as firewalls and intrusion detection systems, to defend internal assets from threats, in third party interconnected networks. Organizations use system security elements such as antivirus and content filtering to mitigate risks from viruses, spyware and trojans.
Network and system changes are generally prone to configuration changes, deviations from the industry best practices and incorrect patch levels. It is important to ensure that the network and system security framework is properly designed and tested regularly.
Our Network and System Security Services ensures:
- Clear understanding of current network security posture
- Proactive identification of network security risks, threats and vulnerabilities
- Effective utilization of network IT infrastructure investments
- Reduce operational impact to the network
Our Network and System Security Service suite includes:
- Network and System Security Assessment
Our assessment service provides you with a comprehensive view of the security of your networks, systems and datacenter. Our services benchmark the current state of your security posture against the industry best practices and the desired level of protection based on your risk profile. We provide you with a set of recommendations and roadmap to enhance your organizations security posture.
Our Network and System Assessment and Data Center Assessment services assess the overall security posture of the Network and System infrastructure within an organization. We assess the information security management, business continuity framework, security design and security architecture. We use a defense in depth model and operations through a review of the adequacy and effectiveness of documented and implemented controls.
Our review covers all critical areas such as, Local Area Network (LAN), Wide Area Network (WAN), architecture and design, logical security of network components such as switches, routers firewalls, Virtual Private Networks (VPNs), backup and recovery, change, release, configuration, incident and problem management.
Additionally, we review technical controls such as patch management and anti-virus updates, device management and monitoring. Our reports compare the current security posture to best practices, identify the gaps in the security framework and implementation and suggest appropriate mitigation measures.
The IT infrastructure has various vulnerabilities arising due to configuration mismatch and insecure coding practices. Our Vulnerability Assessment service identifies vulnerabilities through use of a combination of vulnerability scanners. Our security analysts analyze the tool output in detail, align with threat scenarios relevant to the organization and provide a comprehensive report of vulnerable systems and mitigation measures.
- Network and System Security Architecture and Design
Secure network design plays an important role in protecting information. With the availability of sophisticated tools, attacks and exploits have become simpler. It is becoming a challenge to build a secure network. A secure network is designed and built to address the current and future needs of an organization. We use a defense in depth approach to ensure consistent level of security across various network tiers and elements. Our services assist the architects at the customer organization to design their network and security architecture.
- Security Product Implementation and Platform Hardening
Our professional services enable organizations to set up and operate products such as firewalls, Intrusion Detection Systems (IDS), antivirus and anti-spam software, in the existing IT platforms. Our consultants augment existing security teams for project management to enhance the support, maintenance and system integration during service transformations.
Identity Access Management
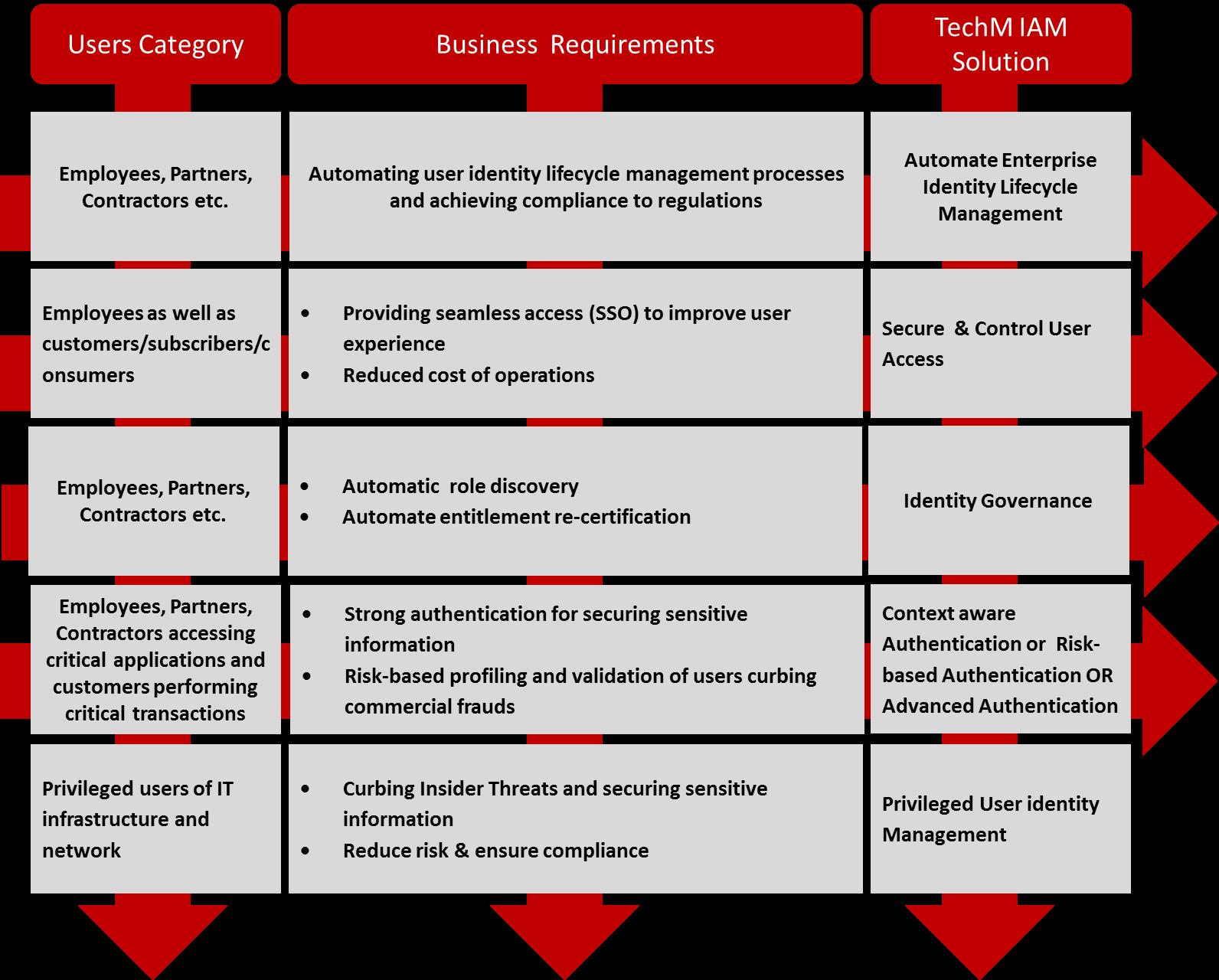
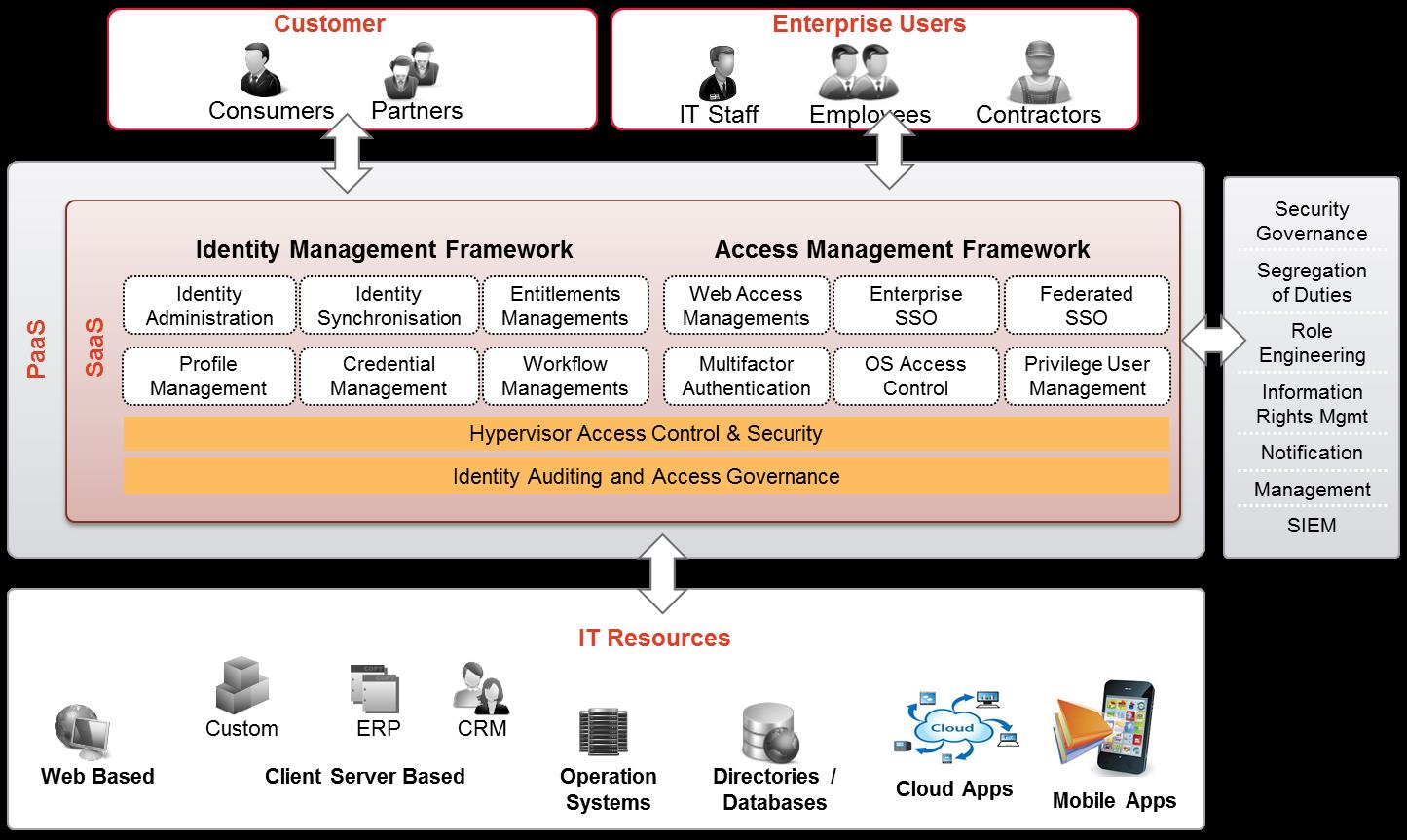
Identity and Access Management (IAM) as a security solution enables customers, partners and employees to access business and enterprise applications in a secure and compliant manner. An IAM solution flexible enough to enable this access is a prerequisite for an IT transformation journey that allows employees to bring their own devices to work (BYOD), to reap the benefits of agility and reduced cost using cloud services (identity as a service) and to enhance user experience across all electronic channels. To support increasing e-commerce using internet, organizations must enhance the consumer experience and federate with partners in an efficient, secure and cost-effective manner. To manage users and comply with regulations, it is essential to automate user identity lifecycles processes User identity will soon be the cornerstone of all big data projects enabling organizations to personalize services across a mass customer base.
atom is an experienced IAM system integrator with an experience in deploying IAM solutions for some of the largest and most demanding customers across the world. We have devised solutions that scale, methodologies that facilitate rollouts in complex estates and out-of-the-box components for quicker implementations. Our goal is to help reduce implementation risks and advice our clients on the best method to implement and support the IAM program. The IAM Practice highlights are as follows:
- Large team of qualified IAM consultants and SI specialists
- Expertise in all major IAM functionalities – Identity management, role management, access management, SSO, federation, directory technology, privilege user management
- Expertise in all leading IAM products with alliance & partnership with major IAM product suites
- E2E IAM services offered – Consultancy, System Integration and Support
- Extensive experience across various industry domains
- Multi-product IAM lab, Cross Platform CoEs
- Proven Methodology – Envision, Enlighten, Transform, Maintain
The Service portfolio for IAM services is aligned with the overall objectives of the Security practice – it covers assessment, design, build and management of IAM solutions as follows:
IAM Consultancy – We provide IAM Consultancy services in the following areas:
• Analyzing identity-related business and technical requirements
• Architecting and designing a best-fit IAM solution covering the lifecycle of:
• Identity management factors such as identity provisioning and de-provisioning, registration, role change events, self-care and password management
• Access management factors such as authentication, authorization and federation
We architect, plan and support the implementation of IAM infrastructure to ensure enhanced return on investment to our customers.
IAM SI – We provide full lifecycle deployment of Identity and Access Management solutions that include transitioning from legacy IAM systems, developing workflows, connectors, data migration scripts, and integrating with Service-Oriented Architecture (SOA). Our integration methodology, rollout plans, comprehensive installation and configuration services help speed up deployment time and minimize disruption to existing systems.
We also develop add-on modules and single sign-on plug-ins for our customers and suppliers to speed up federation.
IAM Operations – We take total ownership of managed operations – 24X7 SLA based support services for large centralized IAM capabilities. Support services cover fault and change management, platform management, migration, upgrade, vendor management and policy administration. Additionally, the services cover ongoing small enhancements to the IAM infrastructure, such as the development or modification of connectors and workflows.
atom’s IAM propositions for our customers
Organizations need to simplify application estates through a centralized IAM framework. The framework will simplify user identity lifecycle process, improve user experience through single sign-on, enhance the audit process and facilitate quick application rollouts with lower operational and development costs.
Our Identity and Access Management Services ensure:
• Fully automated user provisioning, thus increasing the employee productivity
• Facilitate seamless access to all applications that improve user experience
• Reduce help-desk support costs and risk of identity theft
• Enhance the ability to comply with corporate security policies and regulation requirements
We have been working as system integration partner/alliance with all IAM product vendors as below
1. Computer Associates – GTM partnership globally
2. Oracle – Platinum partner globally
3. NetIQ – Gold Partnership globally
4. IBM – Alliance globally
Apart from this we have alliance partnership with Microsoft and have also implemented the OpenSource access management platform based on OpenAM (supported by ForgeRock)
We have built a Multi-product IAM lab, Cross Platform CoEs for all the products mentioned above.
Managed Security Services
Managed Security Services
Organizations are increasingly outsourcing information security operations to telecommunication companies and specialist Managed Security Service Providers (MSSP). Customers require cost-efficient pricing, stringent Service Level Agreement (SLA) based support, 24×7 specialized expertise and support for a heterogeneous product set.
The increasing competitiveness of the MSSP industry, shortage of skilled security analysts and high operational costs have limited the scaling and service expansion plans of most MSSPs. We provide a remote, fully-managed, white-labeled Security Operation Center (SOC) that enables MSSPs to rapidly set up an alternate SOC with reduced operations costs. The SOC will support on-demand scalability, expand the service set and enhance geographic footprint.
Our Managed Security Service assists you to run and globalize a successful MSSP business based on:
- 50 percent reduction in security operation cost to boost profitability
- Re-use existing MSSP Capital Expenditure (CAPEX) investment
- Expand product portfolio to enable larger deal sizes
- Flexible ramp up and ramp down of the security analyst team
Our Managed Security Services offerings include:
- Professional Services
Our professional services enable MSSPs to set up and operate SOCs. In addition, our services will enable MSSPs to augment existing security teams for project management and enhance the support, maintenance and system integration during service transformations.
- Remote Security Operation Center
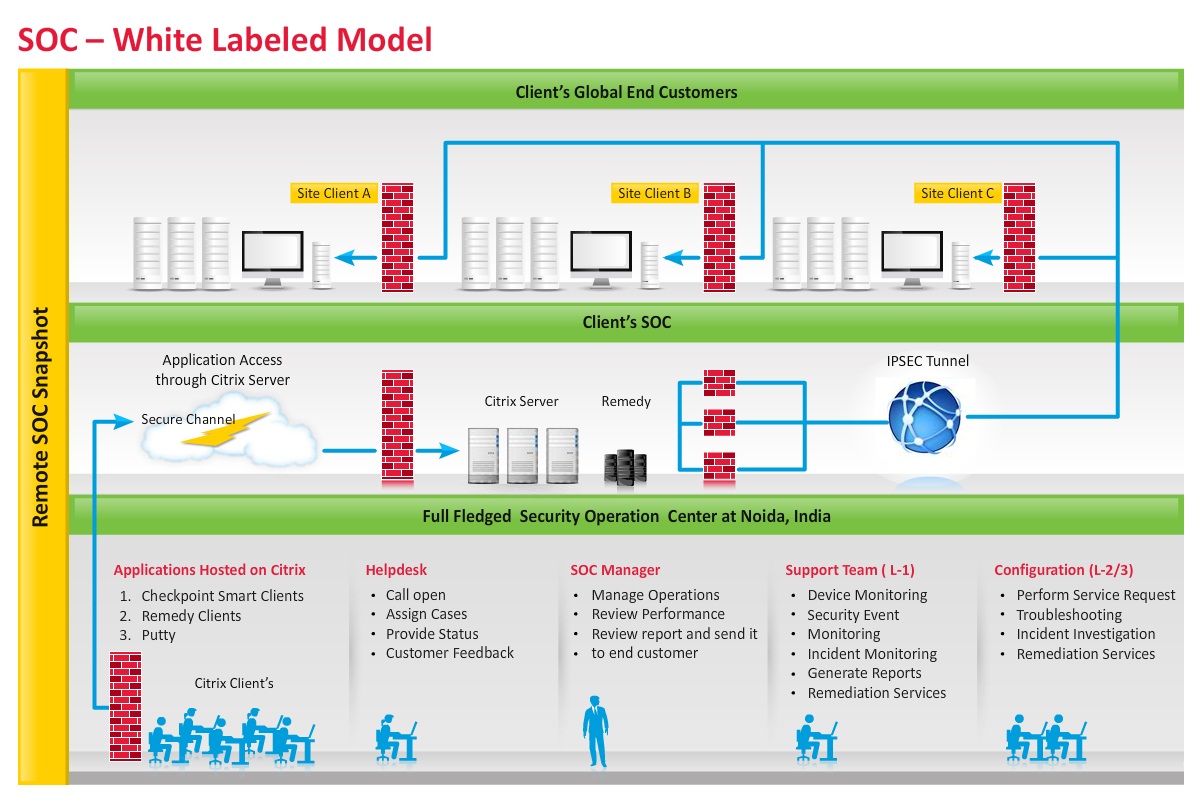
Our SOC services will enable us to set up and run a Level 1, Level 2 and Level 3 remote SOC on a 24×7 and 365 days support. Using the SOC we can provide IT security management and monitor services with the existing technology infrastructure of the MSSP. Transition and operations are undertaken using our proven Information Technology Infrastructure Library (ITIL)-based master framework to support back-to-back customer SLA and product vendor management.
A typical remote SOC setup, the connectivity with MSSP SOC and MSSP global customer base
A typical service portfolio and representative technology capability
IT Infrastructure Operation Management
We offer Consultancy, implementation and management for all infrastructure applications, including Enterprise Systems Management and Information Technology Service Management systems. These systems are critical for the day-to-day information technology operations of global customers and we have developed capabilities to support all the leading vendor solutions in this domain including, CA, BMC, HP, IBM and Microsoft.
We strongly believe the future of efficient information technology operations is dependent on a strong service automation platform and the ability to provide customers with an end-to-end service view. We have invested in a Service Automation Platform and a Service Performance Management Platform that enables our customers experience a new level of service efficiency and management.
atom Enterprise Systems Management (ESM) service focus on addressing critical needs of customer enterprise towards implementation and operations of ESM Tools.
atom collaborates with you to create an ESM tools service strategy that will ensure maximum infrastructure availability, data protection, business application performance. It will also provide visibility towards highly available infrastructure & towards increasing the responsiveness for better application performance with real time dashboards and reporting.
atom’s offers Consultancy, implementation and management for all infrastructure applications including Enterprise Systems Management and IT Service Management systems. These systems are critical for the day-to-day IT operations of Enterprise Customers and Atom’s has developed capabilities to support all the leading vendor solutions in this domain including, CA, BMC, HP, IBM and Microsoft.
We strongly believe the future of efficient IT operations is dependent on a strong service automation platform and the ability to provide customers with an end-to-end service view. We have invested in a Service Automation Platform and a Service Performance Management Platform to take our enterprise customers to a new level of service management.
Our services in Enterprise Management include:
- Plan(Consultancy)
- Assessment Services
- Business Services Management
- Assessment Services
- Build(Design & Implement )
- Solutions
- Service Desk & ITIL Processes
- Monitoring & Event Management
- End User Performance Management
- Business Performance Management
- Application Performance Management
- Service Reporting Portal
- Process Automation
- Solutions
- Run (Managed Services)
- Remote Service Management
- IT Service Management
- Enterprise System Management
- Remote Service Management
Business Issues addressed:
atom recognizes the various potential challenges our customers face in their daily routine of managing complex IT functions to drive their core business services. Atom’s Business Service Management solutions reduces IT complexities, by breaking away technology focused silos to a business driven IT environment that address the challenges like
- Process standardization & automation, Business Services Assurance.
- Seamless integration of disparate technological components to achieve business goals.
- Optimization of IT Services towards supporting the business priorities.
- Business oriented IT Services transformation from IT driven Business.
- Need for intrusive Real-Time Performance and Availability Solution.
- A consistent, holistic view of the enterprise from multiple dimensions.
- A consistent management methodology of the enterprise in terms of reliability, availability, performance, and supportability (RASP) that is meaningful at the various dimensions of the enterprise.
- A consistent way of defining the overall quality of service measurements, using models that are meaningful to the respective stakeholders.
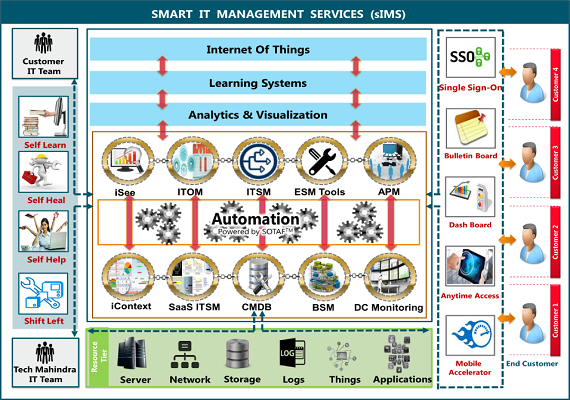
sIMS- Smart IT Management Services
sIMS- Smart IT Management Services
In this digital era characterized by accelerating changes, enterprises are struggling with the following IT management challenges:
- Multiple IT management tools operating in silos. On-going management of these tools is too time-consuming, risky, expensive, and complex leading to constant chaos, fire drills, and wastage of time.
- Pervasive computing (hosted, on-premise or cloud) adds to the existing complexity of IT management environment increasing the cost of IT operations and service management.
- Need of organizations to analyse, anticipate and remediate infrastructure and applications health over hosted, on-premises or on traditional Data Centers.
- Around 80% of the activities in IT Operations are procedural and repetitive. IT Operations is still people centric owing to lack of automation.
- 80% of outages impacting mission-critical services are caused by people and process issues, and more than 50% of those outages are caused by change/configuration/release integration and hand-off issues. These outages result in revenue and productivity losses.
- Upcoming IoT deployments will generate large quantities of data that needs to be processed and analysed in real time. This will increase workloads of data centers, leaving providers facing new service management and operational challenges.
sIMS is a Unified and Flexible IT service and operations management platform, from traditional IT management to Intelligent Management Platform of Things. sIMS is a next generation management platform which:
- Reduces operational complexities with single management interface
- Eliminates cost with customizable automation packages
- Improves IT service and operations management with In-Built best practices
- One platform supporting applications, infrastructure and things
Solution Benefits
- Elimination of upto 50% of the existing cost spent towards service and operation management of the IT environment.
- Improved service and operations management cycle time upto 60 % from current level.
- Plug and play architecture to service customised requirements and building on existing investments.
- Application availability time can be improved up to 70%.
- Multi-tenant environment leading upto 10-15% improved operational efficiency.
- We have pre-built customizable automation templates for approximately 1400 business and 150 IT processes and sub-processes.
- Integrated service bus delivers an easy–to–use unified platform enabling users to manage and control the entire IT Infrastructure.
- Ability to scale infrastructure elements without a proportionate increase in the support resources.
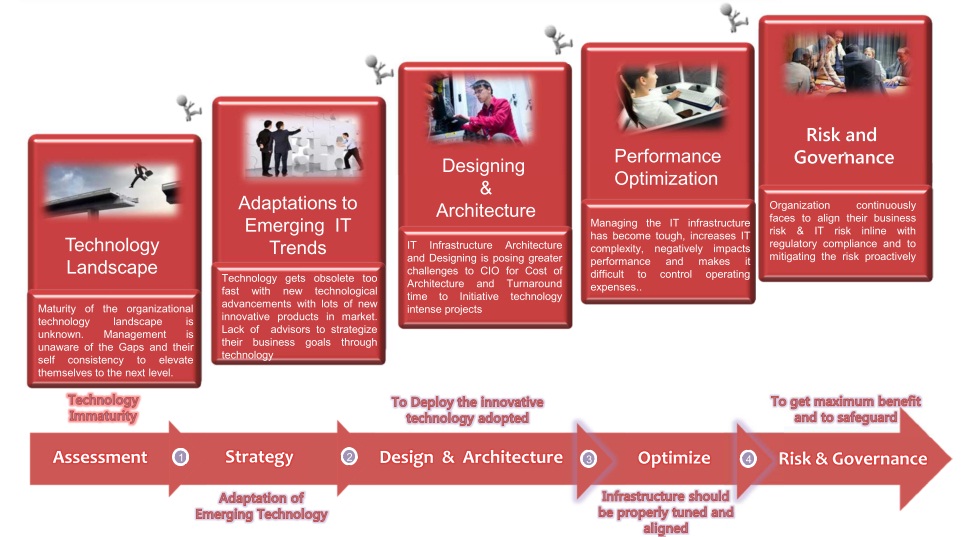
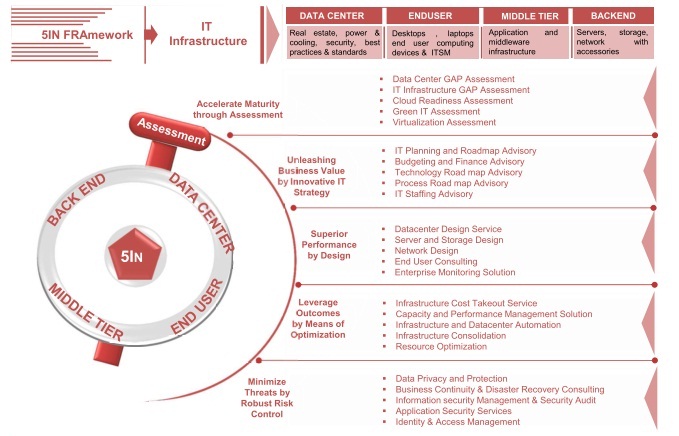
atom Infrastructure Consultancy services helps you develop a roadmap for building a flexible, responsive IT infrastructure aligned with your business goals. We provide comprehensive and lifecycle – oriented IT Infrastructure Consultancy services to meet your unique business requirements leveraging 5IN FRAmework. Our Infrastructure assessment framework addresses optimization and transformation opportunities across your enterprise infrastructure ecosystem to delivers a holistic solution with the following –
- Enhanced Business-IT Alignment
- Improved IT performance
- Optimal Cost savings to release funds for strategic investments
5IN FRAmework of Atom’s divides the entire IT Infrastructure into 4 segments and our 5 Consultancy service offerings cover the entire life cycle of infrastructure management. Major Infra Challenges are addressed through this framework;
We offer managed transformation services leveraging platform that has been developed to meet the scalability, complexity and service performance requirements of enterprise IT services .