Security
Overview
We are a leading Information Security services provider to enterprises worldwide. We specialize in helping our customers implement security transformation plans and maintain an up-to-date security posture in a well-articulated, efficient and meticulous manner, across IT and business functions. Our “Entry-to-Exit” range of service offerings spanning Consultancy, system integration, security testing and security operations, is designed to mitigate external and internal risks for their current and evolving business processes as well as their IT infrastructure, ensuring security completeness for all aspects of the business.
Our philosophy is to be a preferred long-term security partner to our customers and help them implement security solutions in complex estates. Over the last 14 years, we have built an experienced team of over 450 security consultants, customised security solutions, and made investments in Centres of Excellence to assist our customers in achieving a robust security posture. Our clients benefit from engagements covering a wide risk-management strategy with reducing administration, operative costs and improved efficiency.
Services
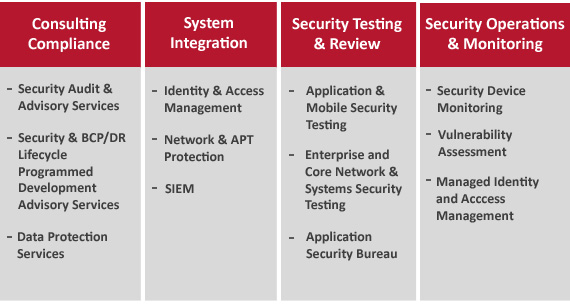
Our value-based partnership approach has been designed to provide our customers with reputation protection, asset protection and compliance. This is achieved through services across the following four categories.
- Consultancy and Compliance services, where we carry out IT risk assessments and benchmarking of organizational security against international standards and best practices. We also help design security frameworks, policies and procedures to uplift the security maturity of an organization
- System Integration services, where we deploy and customize security products across the application estate and network infrastructure
- Security Testing and Review services, where we test the compliance and adherence of enterprise, web and mobile applications to organizational security policies, regulatory requirements and industry standards
- Security Operations and Monitoring services, where we provide round-the-clock management and monitoring services for security infrastructure
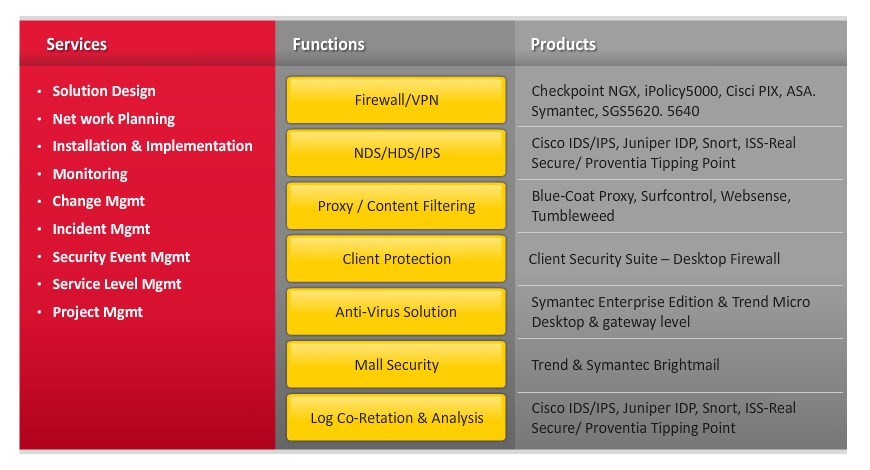
Individual services under these categories are listed in the table below.
Additional detail on key services is available from the links below
- Consultancy and compliance
- System integration
- Identity and access management
- Enterprise and mobile application security testing
- Network and system security
- Managed security services
Preparing for the future
Security has to constantly keep pace with advancements in technology. As our customers adopt newer technologies to do their business, we invest in developing new solutions or extending existing solutions to provide them with continued security cover for their business activities. Some of the areas where we are exploring new solutions include:
- Converged Authentication:
Enabling organisations to provide a superior user-experience for their customers by giving them a single method to identify and authenticate themselves irrespective of the channel they use to transact. For instance, banking customers who have to remember multiple passwords for online banking, phone banking and for branch-based services, can now get authenticated using a single mechanism
- Mobile Apps’ Security:
With smartphones crossing the boundaries between personal and professional use, mobile apps that power the ubiquitous smartphones are also a key focus for malware. We offer a hosted service that scan mobile apps for the potential rogue behaviour, and our mobile R&D team continues to optimise the detection heuristics to stop even potential zero-day attacks.
Contact us for more information about our current and future-ready services.
Service Offerings
Security Governance Compliance
With the exponential increase in digitization of information, regulators have opted for stringent data privacy and fraud prevention measures. Customers have become increasingly conscious of data security, and direct the organizations to include Information Security (IS) as cost of doing business.
Most large organizations have security and business continuity systems and process in place. These systems have grown over time and have been influenced by the perception of security among different function owners. New regulations have built another layer of patchwork for risk compliance
Since security systems have become expensive to maintain, they are inconsistent across the organizations and are not fully compliant to best practices. Alignment of existing security processes with broader organizational initiatives such as Control Objectives for Information and Related Technology (COBIT) and Information Technology Infrastructure Library (ITIL) requires more effort and investment.
We have comprehensive suite of Security Governance, and Risk and Compliance services that assist organizations to review the security framework and the operational controls and to continuously assess and manage the security level.
Our Security Governance and Compliance Services ensure that your organizations security framework is aligned to the business objectives. Our services will help organizations to achieve:
- Unified assessment for security, business continuity and information technology service management
- Smooth integration of Security framework with the information technology and business initiatives
- Certification to international standards such as International Organization for Standardizations ISO 27001
Our Security Governance and Compliance services include the following:
- Information Security Governance Services
The service assists the organizations in implementing the risk- and- standard- based security governance and management framework based on the industry best practices such as ISO 27002. Our security consultants use a combination of techniques such as assessing security risk, identifying the relevant gaps to in the standards, devising the process and technical control framework, providing implementation, handholding support and final pre-certification audits. Security Governance is implemented by institutionalizing security across the organization through various programs and making it measurable.
- Information Risk Assessment
The Risk Assessment service identifies the potential risks to all critical information assets in an organization. Our service covers all electronic and non-electronic information assets and is benchmarked against the industry best practices such as BS 7799: Part 3 ISO 13335 and NIST. A risk profile shows all high-impact risks with suitable guidance to plan for suitable and cost-effective measures.
- Information Security Assessment
Our Information Security (IS) Assessment provides a comprehensive view on the current state of the organizations security posture. Existing security processes are assessed for adequacy and operational effectiveness. The scope of assessment encompasses analyzing applicable security controls for critical business processes, IT operations, outsourcing, business continuity, network and applications.
- The assessment is carried out following the industry’s best practices and standards such as ISO 27002, National Institute of Standards and Technology (NIST) and Computer Emergency Response Team (CERT) for in-depth coverage of all aspects. A security profile is generated comprising of the strengths and weaknesses in each security process across the organization. We provide a report of the identified security vulnerabilities and process gaps, prioritized by the business impact, and with appropriate recommendations.
- Security Assessment Services
The Security Assessment Service provides a complete view of the organizations security through a holistic assessment of security processes. Our services benchmark the existing state of the organizations security posture against the industry best practices and the desired level of protection based on the risk profile.
- Information Security Audits
The Audit Service focuses on the risk compliance aspects of security. It covers the regulatory compliances, adherence to internal policies and procedures, second party vendor audits, readiness checks for certifications, standards such as ISO 27001 and compliances such as Sarbanes Oxley (SOX) and Payment Card Industry (PCI). The audit findings help organizations to identify the compliance level and areas of improvement.
- Security Consultancy Services
The Security Governance, Risk and Compliance Consultancy Services helps create and maintain an optimal security framework for the organization.
- Compliance Services
The Compliance Services enable organizations to prepare for various compliances such as SOX and Payment Card Industry Data Security Standard (PCI DSS). Internal Control framework for all in-scope IT assets are developed based on the scope defined by the organizations auditors. We assist in the implementation and testing of these controls.
- Information Security Support Service
Most organizations face the challenge of maintaining the security baseline by ensuring that the function owner adheres to the security policies. We assist customers in managing Information Security (IS) by providing security support to function owners. Our consultants interpret the organizations security policy and work to translate this into functional tasks (e.g. security controls in application design and environments). We also support security and internal audit functions by providing policy and process maintenance and audit support.
- Role-based Access Consultancy Service
Role-based access with legitimate authority on organization applications is the most important aspect of IS. Our Role-based Access Consultancy Service helps organizations to train the roles and access the matrix for enterprise applications, ensuring proper Segregation of Duty (SoD).
System Integration
We know from our experience gained in several large-scale security system integration projects, that an optimal system integration strategy is crucial to the overall success of the business. We have the right tools, templates and industry best implementation methodologies to meet customers information and data security requirements. We offer a complete set of services in the following areas:
- Endpoint security
- Network security
- Identity and Access Management (IAM) implementation
- Content and Uniform Resource Locator (URL) filtering
- Log management
The telecom sector faces major challenges such as adopting complex technologies, ever changing business environments and reducing cost. Telecom companies often lack solutions to match the evolution of new technologies and changing business requirements.
We provide system integration expertise to ensure that the technology is strategically aligned to meet the business objectives regardless of the size and nature of the organization.
Our certified processes and service experience indicate the success achieved in executing large turnkey security system integration projects. Our strategic alliances with leading technology players enable us to deliver cost-effective integration services that are steady, scalable, effective, efficient and innovative.
Application Security Consultancy
Security of application assets is a prime concern for organizations. Lack of appropriate application security controls leads to regulatory non-compliance, business continuity failures and data compromise. An effective end-to-end set of services establishes a holistic application security baseline that mitigates risk.
Our services help enhance the security posture of application assets by systematic reviews and assessments. Our Application Security Services ensure a secure application estate by:
- Identifying and prioritizing the high-risk application assets based on business impact and security vulnerabilities
- Assessing the security level of the application systematically throughout the build cycle
- Establishing a security assurance gate to ensure that the new application code and products are assured prior to deployment
- Ensuring a holistic perspective to application security from business requirements to software coding to operations
Read More...
Our Application Security Consultancy Services include:
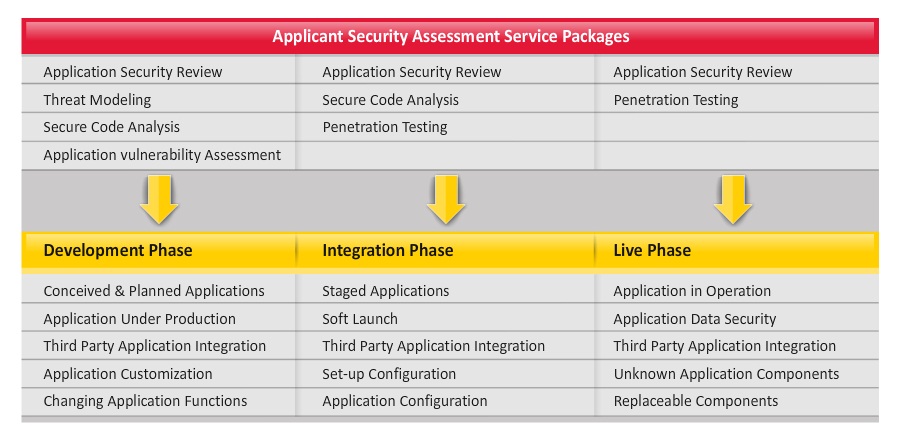
- Application Estate Security Review
Application Estate Security Review is a high-level review to identify and prioritize the high risk application assets within your application estate. The application estate constitutes the business solution consisting of a set of applications, application infrastructure, business workflows, application technologies, organizational strategies and policies, compliance needs, processes, application security governance and operational procedures. - A high-level application estate security review covers the risk compliance and business security system requirements. As integral parts of the application lifecycle, the review secures the development best practices and operation security application frameworks for identity, access, business continuity and monitoring.
- Application Security Assessment
Application Security Assessment is a consultant-driven detailed analysis of an application security.It covers application risks within requirements, code, security control implementation and application infrastructure. Our consultants use a combination of techniques such as Threat Modeling, Code Analysis, Vulnerability Assessment and Penetration Testing. These techniques are used to identify application security vulnerabilities, risk levels and mitigation steps. Our assessment services can be combined with the Application Estate Security Review to provide a holistic view and roadmap.
- Secure Code Analysis
Security Code Analysis is a comprehensive security assessment and analysis of application code that focuses on application security considerations, such as secure programming, business-driven application security policies, information protection needs, authentication needs, access controls, authorization and trusted computing needs.
- Application Security
Application Security review covers a detailed assessment of security requirements, architecture and design, implementation, testing plan and deployment and application infrastructure and components.
- Threat Modeling
A Threat Model assesses an application or its components for potential threats to provide threat ratings based on the criticality of the threat and possible attack exposure. Our process comprehensively records all the application components such as entry points, exit points, dependencies, information and data flow, user roles, protected resources, attack path and mitigation objectives.
- Application Security Testing
An application and its components are inspected for level of their resilience to possible application security threats. Application Vulnerability Assessment identifies the security issues that may expose the business to risk due to internal threats. Penetration Testing identifies vulnerabilities in the web applications that could be exploited through internet facing components.
- Application Security Assurance Service
Application Security Assurance Service involves setting up of comprehensive security gate within our customer’s environment, which analyzes the application estate for vulnerabilities, threats and risks. Our service provides recommendations for risk mitigation using a combination of assessment service components. The assurance service provides a periodic assessment of the application estate security posture to maintain the business risks to minimum.
Network System Security
Large organizations use network security systems such as firewalls and intrusion detection systems, to defend internal assets from threats, in third party interconnected networks. Organizations use system security elements such as antivirus and content filtering to mitigate risks from viruses, spyware and trojans.
Network and system changes are generally prone to configuration changes, deviations from the industry best practices and incorrect patch levels. It is important to ensure that the network and system security framework is properly designed and tested regularly.
Our Network and System Security Services ensures:
- Clear understanding of current network security posture
- Proactive identification of network security risks, threats and vulnerabilities
- Effective utilization of network IT infrastructure investments
- Reduce operational impact to the network
Read More...
Our Network and System Security Service suite includes:
Network and System Security Assessment
Our assessment service provides you with a comprehensive view of the security of your networks, systems and datacenter. Our services benchmark the current state of your security posture against the industry best practices and the desired level of protection based on your risk profile. We provide you with a set of recommendations and roadmap to enhance your organizations security posture.
Our Network and System Assessment and Data Center Assessment services assess the overall security posture of the Network and System infrastructure within an organization. We assess the information security management, business continuity framework, security design and security architecture. We use a defense in depth model and operations through a review of the adequacy and effectiveness of documented and implemented controls.
Our review covers all critical areas such as, Local Area Network (LAN), Wide Area Network (WAN), architecture and design, logical security of network components such as switches, routers firewalls, Virtual Private Networks (VPNs), backup and recovery, change, release, configuration, incident and problem management.
Additionally, we review technical controls such as patch management and anti-virus updates, device management and monitoring. Our reports compare the current security posture to best practices, identify the gaps in the security framework and implementation and suggest appropriate mitigation measures.
The IT infrastructure has various vulnerabilities arising due to configuration mismatch and insecure coding practices. Our Vulnerability Assessment service identifies vulnerabilities through use of a combination of vulnerability scanners. Our security analysts analyze the tool output in detail, align with threat scenarios relevant to the organization and provide a comprehensive report of vulnerable systems and mitigation measures.
Network and System Security Architecture and Design
Secure network design plays an important role in protecting information. With the availability of sophisticated tools, attacks and exploits have become simpler. It is becoming a challenge to build a secure network. A secure network is designed and built to address the current and future needs of an organization. We use a defense in depth approach to ensure consistent level of security across various network tiers and elements. Our services assist the architects at the customer organization to design their network and security architecture.
Security Product Implementation and Platform Hardening
Our professional services enable organizations to set up and operate products such as firewalls, Intrusion Detection Systems (IDS), antivirus and anti-spam software, in the existing IT platforms. Our consultants augment existing security teams for project management to enhance the support, maintenance and system integration during service transformations.
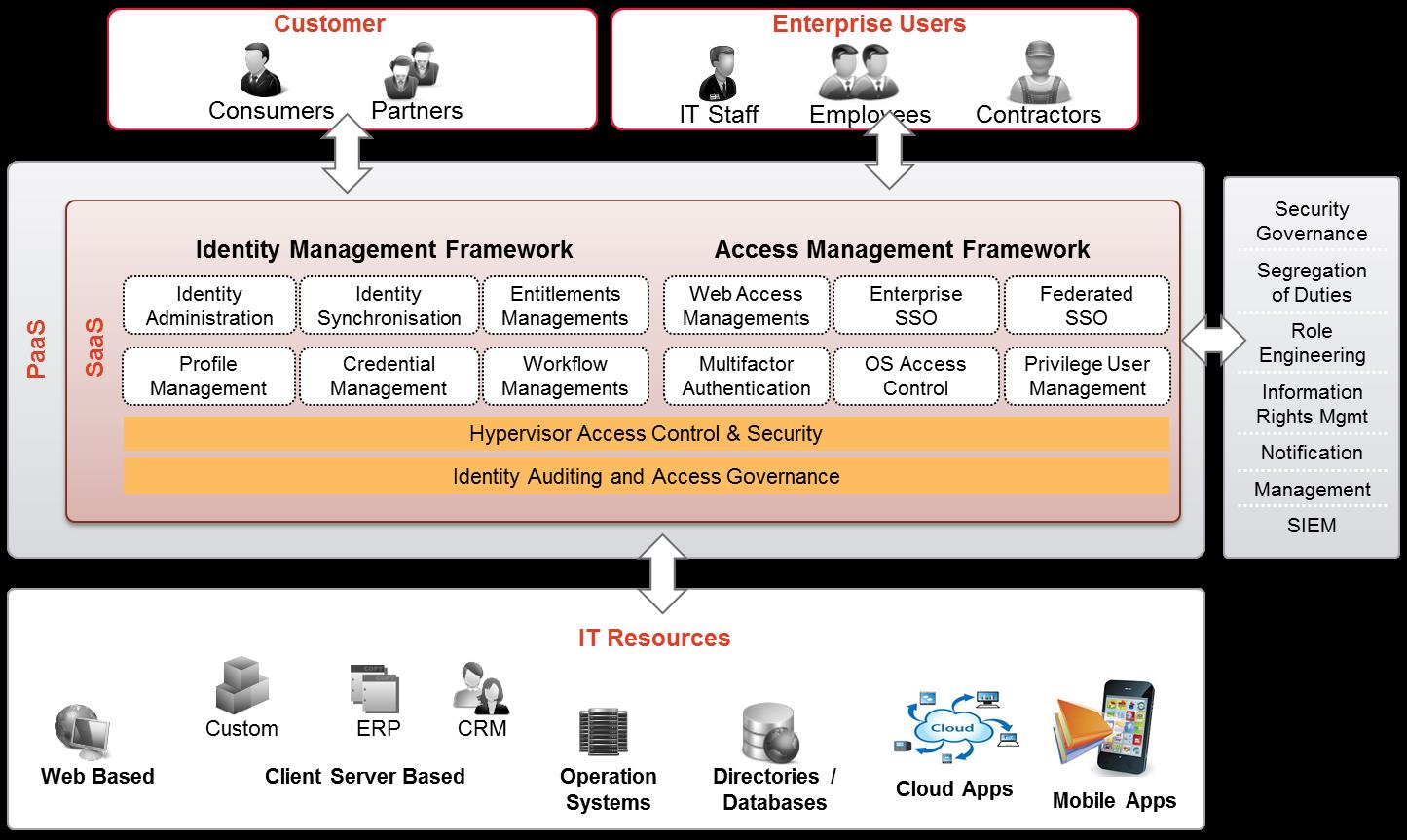
Identity Access Management
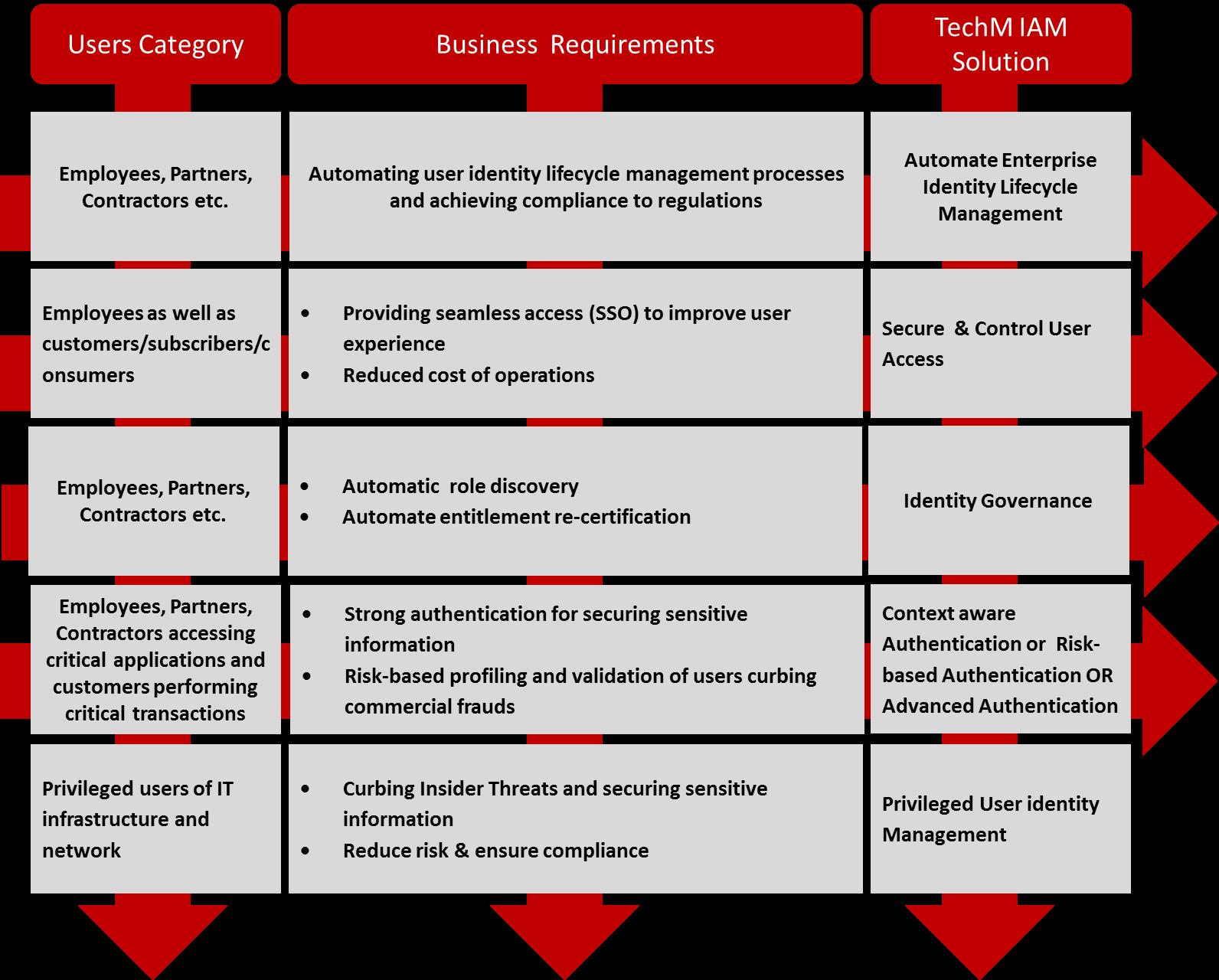
Identity and Access Management (IAM) as a security solution enables customers, partners and employees to access business and enterprise applications in a secure and compliant manner. An IAM solution flexible enough to enable this access is a prerequisite for an IT transformation journey that allows employees to bring their own devices to work (BYOD), to reap the benefits of agility and reduced cost using cloud services (identity as a service) and to enhance user experience across all electronic channels. To support increasing e-commerce using internet, organizations must enhance the consumer experience and federate with partners in an efficient, secure and cost-effective manner. To manage users and comply with regulations, it is essential to automate user identity lifecycles processes User identity will soon be the cornerstone of all big data projects enabling organizations to personalize services across a mass customer base.
atom is an experienced IAM system integrator with an experience in deploying IAM solutions for some of the largest and most demanding customers across the world. We have devised solutions that scale, methodologies that facilitate rollouts in complex estates and out-of-the-box components for quicker implementations. Our goal is to help reduce implementation risks and advice our clients on the best method to implement and support the IAM program. The IAM Practice highlights are as follows:
- Large team of qualified IAM consultants and SI specialists
- Expertise in all major IAM functionalities – Identity management, role management, access management, SSO, federation, directory technology, privilege user management
- Expertise in all leading IAM products with alliance & partnership with major IAM product suites
- E2E IAM services offered – Consultancy, System Integration and Support
- Extensive experience across various industry domains
- Multi-product IAM lab, Cross Platform CoEs
- Proven Methodology – Envision, Enlighten, Transform, Maintain
Read More...
The Service portfolio for IAM services is aligned with the overall objectives of the Security practice – it covers assessment, design, build and management of IAM solutions as follows:
IAM Consultancy – We provide IAM Consultancy services in the following areas:
• Analyzing identity-related business and technical requirements
• Architecting and designing a best-fit IAM solution covering the lifecycle of:
• Identity management factors such as identity provisioning and de-provisioning, registration, role change events, self-care and password management
• Access management factors such as authentication, authorization and federation
We architect, plan and support the implementation of IAM infrastructure to ensure enhanced return on investment to our customers.
IAM SI – We provide full lifecycle deployment of Identity and Access Management solutions that include transitioning from legacy IAM systems, developing workflows, connectors, data migration scripts, and integrating with Service-Oriented Architecture (SOA). Our integration methodology, rollout plans, comprehensive installation and configuration services help speed up deployment time and minimize disruption to existing systems.
We also develop add-on modules and single sign-on plug-ins for our customers and suppliers to speed up federation.
IAM Operations – We take total ownership of managed operations – 24X7 SLA based support services for large centralized IAM capabilities. Support services cover fault and change management, platform management, migration, upgrade, vendor management and policy administration. Additionally, the services cover ongoing small enhancements to the IAM infrastructure, such as the development or modification of connectors and workflows.
atom IAM propositions for our customers
Organizations need to simplify application estates through a centralized IAM framework. The framework will simplify user identity lifecycle process, improve user experience through single sign-on, enhance the audit process and facilitate quick application rollouts with lower operational and development costs.
Our Identity and Access Management Services ensure:
• Fully automated user provisioning, thus increasing the employee productivity
• Facilitate seamless access to all applications that improve user experience
• Reduce help-desk support costs and risk of identity theft
• Enhance the ability to comply with corporate security policies and regulation requirements
We have been working as system integration partner/alliance with all IAM product vendors as below
1. Computer Associates – GTM partnership globally
2. Oracle – Platinum partner globally
3. NetIQ – Gold Partnership globally
4. IBM – Alliance globally
Apart from this we have alliance partnership with Microsoft and have also implemented the OpenSource access management platform based on OpenAM (supported by ForgeRock)
We have built a Multi-product IAM lab, Cross Platform CoEs for all the products mentioned above.
Managed Security Services
Organizations are increasingly outsourcing information security operations to telecommunication companies and specialist Managed Security Service Providers (MSSP). Customers require cost-efficient pricing, stringent Service Level Agreement (SLA) based support, 24×7 specialized expertise and support for a heterogeneous product set.
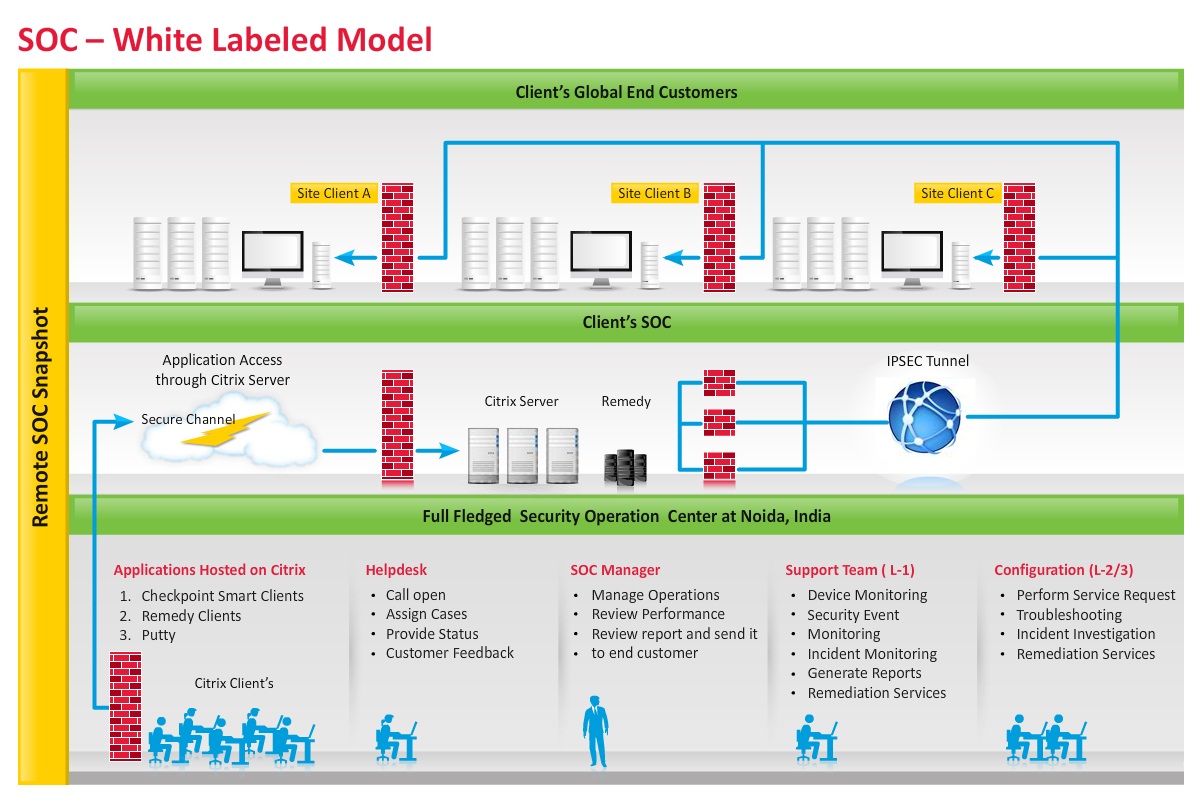
The increasing competitiveness of the MSSP industry, shortage of skilled security analysts and high operational costs have limited the scaling and service expansion plans of most MSSPs. We provide a remote, fully-managed, white-labeled Security Operation Center (SOC) that enables MSSPs to rapidly set up an alternate SOC with reduced operations costs. The SOC will support on-demand scalability, expand the service set and enhance geographic footprint.
Our Managed Security Service assists you to run and globalize a successful MSSP business based on:
- 50 percent reduction in security operation cost to boost profitability
- Re-use existing MSSP Capital Expenditure (CAPEX) investment
- Expand product portfolio to enable larger deal sizes
- Flexible ramp up and ramp down of the security analyst team
Our Managed Security Services offerings include:
- Professional Services
Our professional services enable MSSPs to set up and operate SOCs. In addition, our services will enable MSSPs to augment existing security teams for project management and enhance the support, maintenance and system integration during service transformations.
- Remote Security Operation Center
Our SOC services will enable us to set up and run a Level 1, Level 2 and Level 3 remote SOC on a 24×7 and 365 days support. Using the SOC we can provide IT security management and monitor services with the existing technology infrastructure of the MSSP. Transition and operations are undertaken using our proven Information Technology Infrastructure Library (ITIL)-based master framework to support back-to-back customer SLA and product vendor management.