
Security Testing
Overview
Our Security Testing Group with footprint in all major geographies is a strong team with over 70 highly skilled and experienced security professionals having industry leading certifications.. This dedicated team is led by people with a mission to provide our customers a robust environment to conduct business without worrying about security aspects. In over 10 years, we have helped more than 50 customers in securing applications, complying with standards, implementing secure development practices and mitigating risks.
Why Choose atom?
Our security testing services are backed by:
- Over 70 professionally certified consultants with in-depth experience in different business verticals
- Industry leading certifications, including Certified Information Systems Security Professional (CISSP) , Certified Ethical Hacker (CEH) , and EC-Council Certified Security Analyst (ECSA)
- Over 50 customers, including Tier 1 across telecom; banking, financial services, and insurance (BFSI); manufacturing and government industry verticals
- Vast experience in both open source and commercial industry leading security testing tools such as IBM AppScan, HP WebInspect, Acunetix, Burp Suite, Nmap, Paros, Metasploit Framework
- Empanelled with Indian Computer Emergency Response Team (CERT-In) as an approved Information Security Auditor
Benefits
Having a vast skill and experience base in security services, we can deliver clear business benefits to our customers, including but not limited to:
- Application security testing practices conforming to industry standards
- Research and development backed teams to support new findings and provide expert security testing consultancy
- Cost effective remediation resulting from clear and actionable testing reports
- Reasonable assurance of vulnerability fixes through a round of remediation testing
- Competitive timelines and rates using mature testing and project management practices
- Consistent reporting and documentation through in-house developed tool–ARTfact
Why Choose atom?
Some of value propositions and key differentiators are listed below:
- Security knowledge and expertise in various domains such as telecom; banking, financial services, and insurance (BFSI); healthcare; manufacturing and government sectors at technical, process and operational levels
- Consultants include cross domain experts who provide holistic view of an organization’s security posture
- Certified team of ethical hackers to ensure coverage and quality
- Best in class methodology based on industry best practices and standards such as Open Web Application Security Project (OWASP) , Open Security Testing Methodology & Manual (OSTMM) and National Institute of Standards and Technology (NIST) guidelines
- Tests executed using a combination of open source and commercial tools to ensure optimum results
- World class Vulnerability Assessment Centre (VAC), in India, which is ISO27001 certified facility for remote security testing
- Technical and senior management friendly, easy-to-use security assessment reports with executive summary, detailed test cases and mitigation recommendations
- Cloud based automated mobile application security testing solution–mobiVIGIL–for different mobile platforms
- Automated pre-scans of mobile applications for malwares and malicious intents
- Enhanced business credibility and customer confidence by minimizing mobile application security breaches
- Rapid security testing and assessment of multiple mobile applications
- Ready to use scalable hosted service
- No upfront investment in test labs, tools and man-power
Service Offerings
Risk Based Security Testing
In today’s fast-moving technology marketplace governed by shorter times to market, first mover advantages and cut throat competition, it is very important that we move hand in hand with our customers to make sure their services and products remain secure from the moment they hit go-live. To achieve this, we have integrated security testing into the regular development lifecycle.
Risk-based security testing focuses on validating application conformance to security requirements and application specific security policy. It also identifies potential misuse and abuse of the application functionality. This testing comprises the following steps and uses a combination of manual and tool-based techniques. This activity usually runs parallel to integration testing.
Penetration Testing
A Penetration Test evaluates the security of a network, system or application by simulating attacks by a malicious user or hacker. The process involves attacking the target with or without prior knowledge of the underlying technologies to identify potential vulnerabilities. These may result from poor or improper system configuration, application weaknesses, known and unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures.
This analysis is carried out both for insider (disgruntled employee or contractor) and external attacker and involves active exploitation of security vulnerabilities. All identified security issues are then presented to the management, application and systems teams along with recommendations for their remediation.
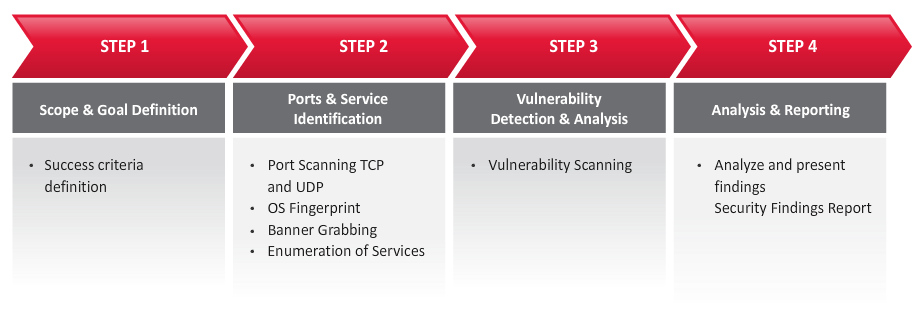
Security Test Offering:
- Automated Mobile Application Security Tests – mobiVIGIL
- We provide automated security testing of mobile applications for different mobile platforms using a cloud based solution known as mobiVIGIL.
- The mobile applications can be uploaded or locations of mobile applications to be tested can be provided to mobiVIGIL.
- A total of 16 categories of automated security tests are performed for various embedded malwares (including embedded spywares, trojans, viruses) and malicious intents in mobile applications (including data privacy issue, data leakage, privilege sms and mms, resource exhaustion, location and tracking, unsolicited network connections, etc.).
- Reports and results are provided in an automated manner with mechanisms to integrate mobiVIGIL application testing interfaces with MDM and various mobile App Test Factories
- Dynamic Profile and Behavior Security Tests
- Mobile applications are dynamically analyzed and tested in lab with various security tools.
- These tests verify security issues including hidden data transfer, unsafe data storage, insecure data transmission, resource exhaustion, insecure file system and database changes, privilege access violations, etc.
- Reports and results are analyzed for each mobile application.
Mobile Application Security Testing – mobiVIGIL
Current Business Problems:
The use of smart phones and mobile applications has significantly increased in the last few years. With the advent of 3G and 4G networks smart phones are increasingly used for financial, business and social transactions, for accessing the Internet and for media consumption. However, the security threats associated with smart phones and for the applications installed in them are quite high. Safety of end user downloading and installing mobile applications, which are distributed through mobile application stores, is a security issue. The mobile application stores need to ensure safe and secure mobile application experience to their customers. Security testing of mobile applications thus becomes an important requirement along with reduced test cycle time.


